

Threat intelligence
The Microsoft Threat Intelligence community is made up of world-class experts, security researchers, analysts, and threat hunters who analyze 78 trillion signals daily to discover threats and deliver timely and timely, relevant insight to protect customers. See our latest findings, insights, and guidance.
Refine results
Topic
Products and services
Publish date
-
 A complex attack chain incorporating the CVE-2018-20250 exploit and multiple code execution techniques attempted to run a fileless PowerShell backdoor that could allow an adversary to take full control of compromised machines.
A complex attack chain incorporating the CVE-2018-20250 exploit and multiple code execution techniques attempted to run a fileless PowerShell backdoor that could allow an adversary to take full control of compromised machines. -

The evolution of Microsoft Threat Protection, April update
Learn about the latest updates to Microsoft Threat Protection and the details of its foundation built on supporting Zero Trust. -

Detecting credential theft through memory access modelling with Microsoft Defender ATP
Microsoft Defender ATP instruments memory-related function calls such as VirtualAlloc and VirtualProtect to catch in-memory attack techniques like reflective DLL loading. -
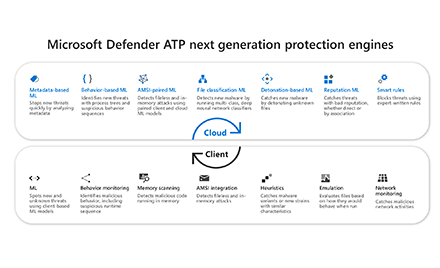
Inside out: Get to know the advanced technologies at the core of Microsoft Defender ATP next generation protection
While Windows Defender Antivirus makes catching 5 billion threats on devices every month look easy, multiple advanced detection and prevention technologies work under the hood to make this happen. -
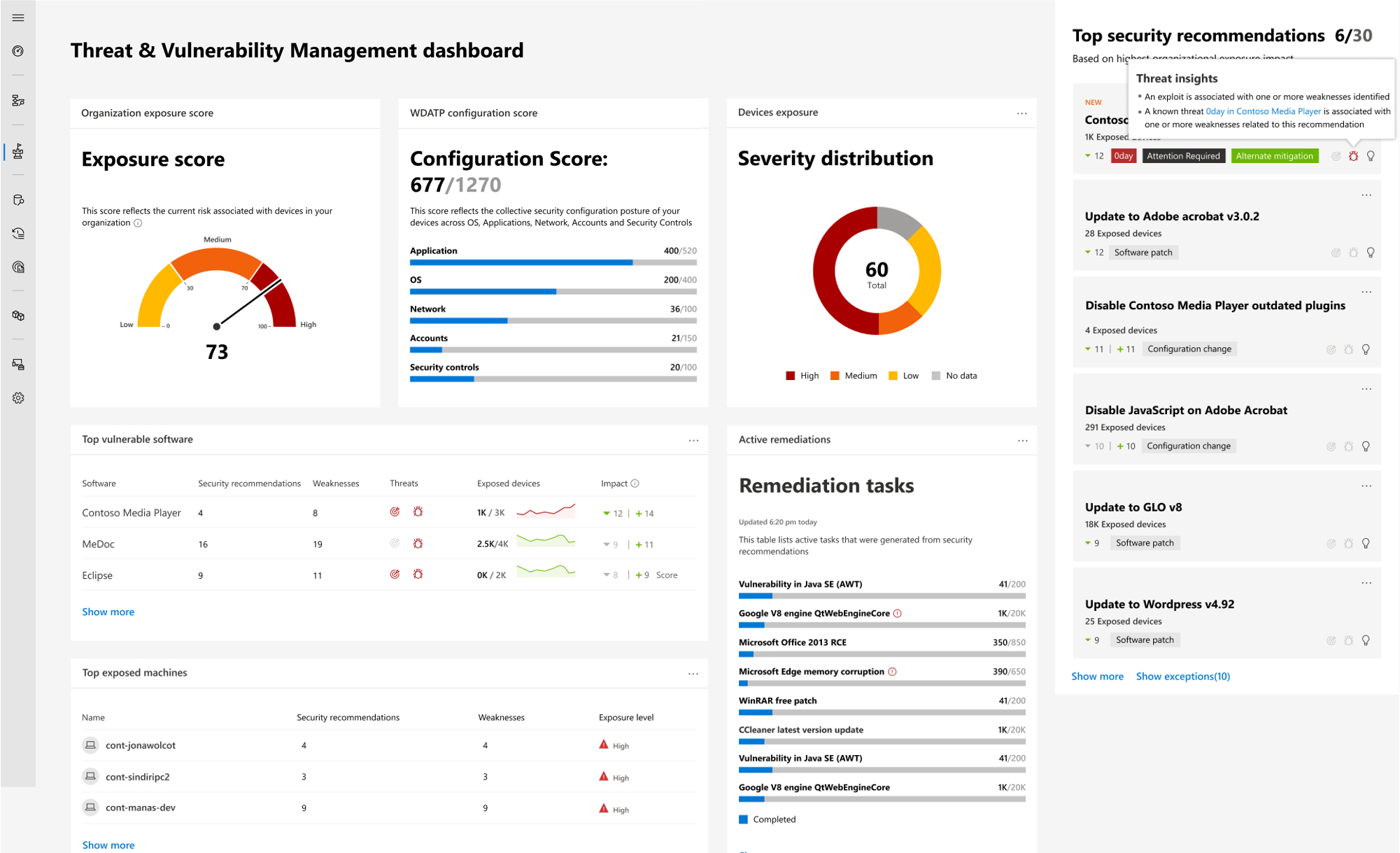
Microsoft’s Threat & Vulnerability Management now helps thousands of customers to discover, prioritize, and remediate vulnerabilities in real time
Microsoft’s Threat & Vulnerability Management solution is generally available! -

Dismantling a fileless campaign: Microsoft Defender ATP’s Antivirus exposes Astaroth attack
Advanced technologies in Microsoft Defender ATP’s Antivirus exposed and defeated a widespread fileless campaign that completely “lived off the land” throughout a complex attack chain that run the info-stealing backdoor Astaroth directly in memory -

New machine learning model sifts through the good to unearth the bad in evasive malware
Most machine learning models are trained on a mix of malicious and clean features. -

How Windows Defender Antivirus integrates hardware-based system integrity for informed, extensive endpoint protection
The deep integration of Windows Defender Antivirus with hardware-based isolation capabilities allows the detection of artifacts of attacks that tamper with kernel-mode agents at the hypervisor level. -

A case study in industry collaboration: Poisoned RDP vulnerability disclosure and response
Through a cross-company, cross-continent collaboration, we discovered a vulnerability, secured customers, and developed fix, all while learning important lessons that we can share with the industry. -

Protect against BlueKeep
DART offers steps you can take to protect your network from BlueKeep, the “wormable” vulnerability that can create a large-scale outbreak due to its ability to replicate and propagate. -

From unstructured data to actionable intelligence: Using machine learning for threat intelligence
Machine learning and natural language processing can automate the processing of unstructured text for insightful, actionable threat intelligence. -

One simple action you can take to prevent 99.9 percent of attacks on your accounts
Learn about common vulnerabilities and what you can do to protect your company from attacks.