

Threat intelligence
The Microsoft Threat Intelligence community is made up of world-class experts, security researchers, analysts, and threat hunters who analyze 78 trillion signals daily to discover threats and deliver timely and timely, relevant insight to protect customers. See our latest findings, insights, and guidance.
Refine results
Topic
Products and services
Publish date
-
 This post is authored by Jonathan Trull, Worldwide Executive Cybersecurity Advisor, Enterprise Cybersecurity Group.
This post is authored by Jonathan Trull, Worldwide Executive Cybersecurity Advisor, Enterprise Cybersecurity Group. -
Twin zero-day attacks: PROMETHIUM and NEODYMIUM target individuals in Europe
Targeted attacks are typically carried out against individuals to obtain intellectual property and other valuable data from target organizations. -
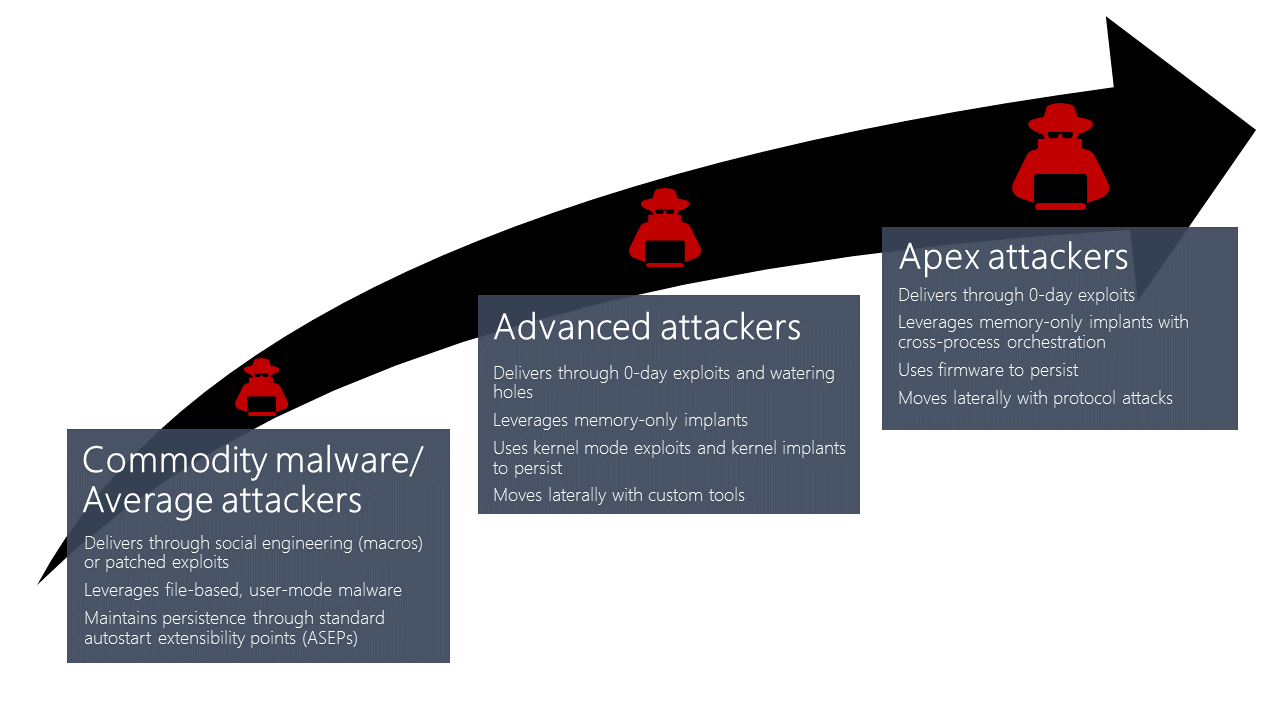
Detecting cyber threats
This post is authored by Joe Faulhaber, Senior Consultant ECG In today’s cyber threat landscape, it’s not a question of if an attack will occur, but who will attack and when. -
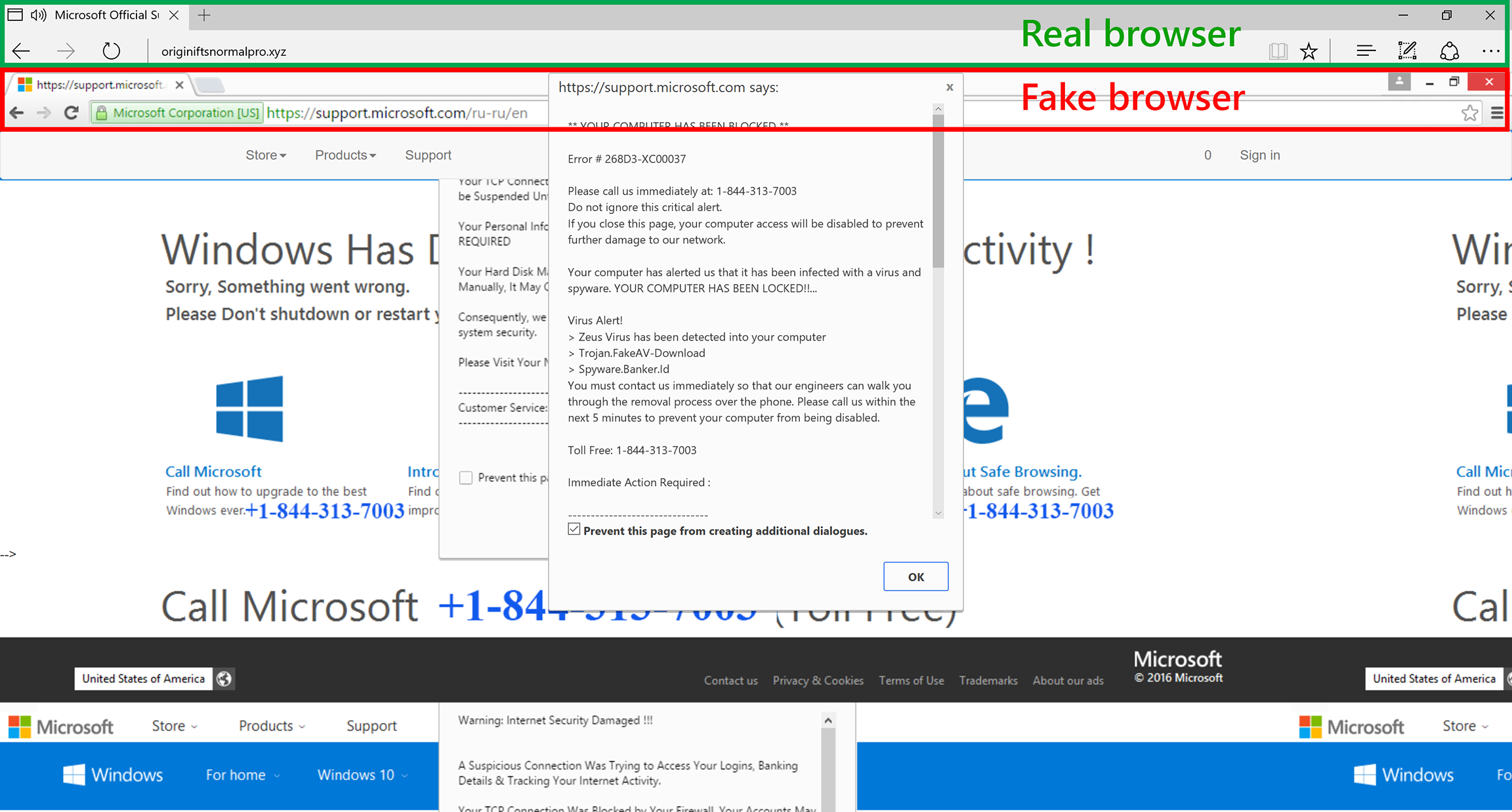
Breaking down a notably sophisticated tech support scam M.O.
The cornerstone of tech support scams is the deception that there is something wrong with your PC. -
Uncovering cross-process injection with Windows Defender ATP
Windows Defender Advanced Threat Protection (Windows Defender ATP) is a post-breach solution that alerts security operations (SecOps) personnel about hostile activity. -
A new best practice to protect technology supply chain integrity
The success of digital transformation ultimately relies on trust in the security and integrity of information and communications technology (ICT). -
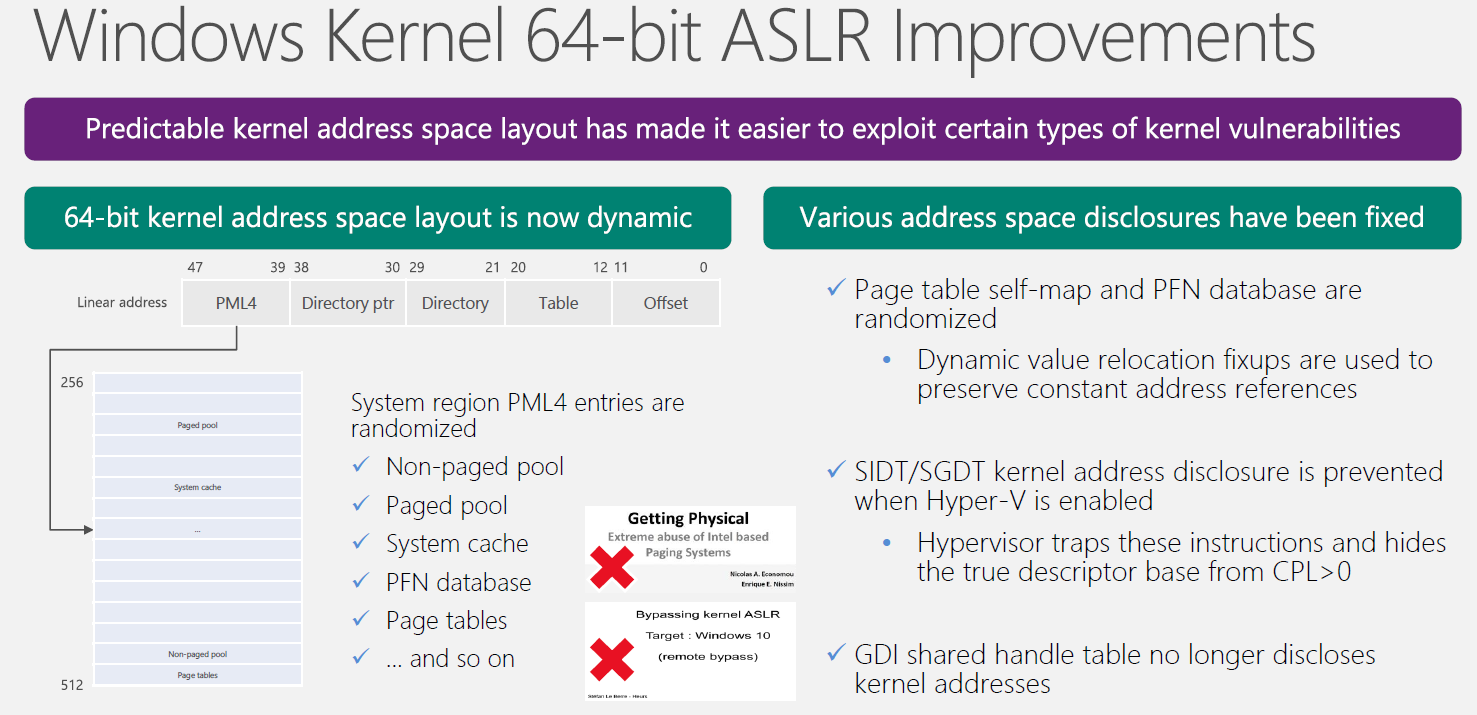
Detecting and mitigating elevation-of-privilege exploit for CVE-2017-0005
On March 14, 2017, Microsoft released security bulletin MS17-013 to address CVE-2017-0005, a vulnerability in the Windows Win32k component that could potentially allow elevation of privileges. -
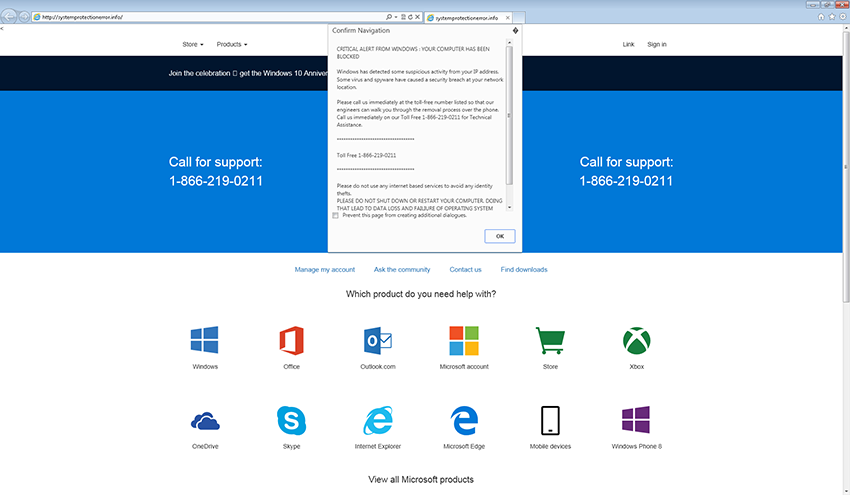
Tech support scams persist with increasingly crafty techniques
Technical support scams continue to evolve, employing more and more complex social engineering tactics that can increase panic and create a false sense of legitimacy or urgency in an effort to get more victims. -
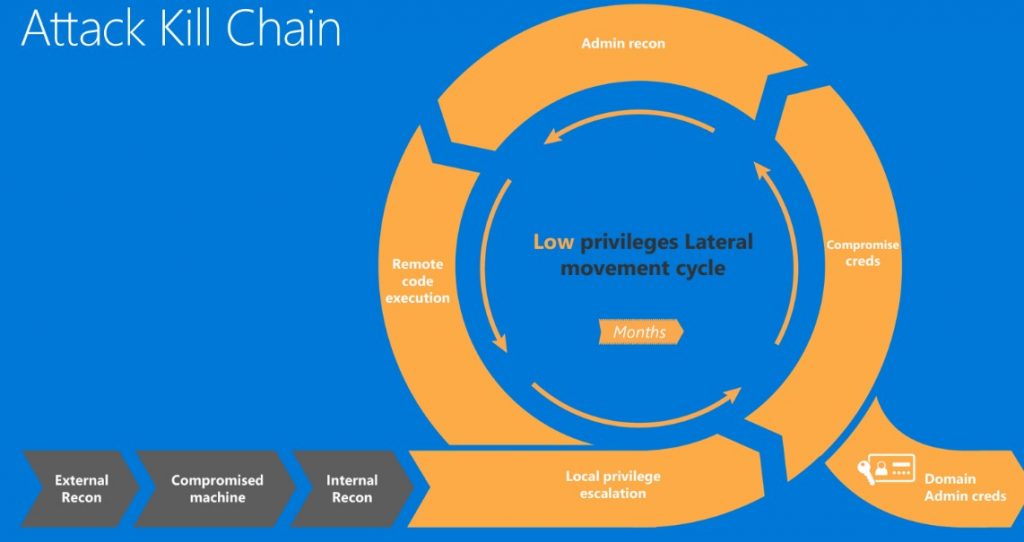
The two-pronged approach to detecting persistent adversaries
Advanced Persistent Threats use two primary methods of persistence: compromised endpoints and compromised credentials. -
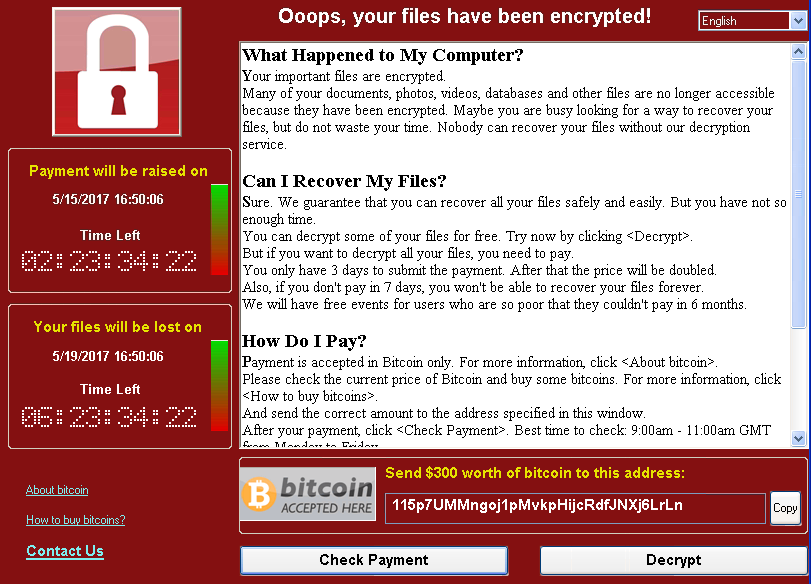
WannaCrypt ransomware worm targets out-of-date systems
In this blog, we provide an early analysis of the end-to-end ransomware attack.