Incident response
Incident response is the process of detecting, investigating, and responding to cyberattacks, security breaches, or IT incidents. Explore the latest trends and intelligence-driven strategies that help you prevent future attacks.
Refine results
Topic
Products and services
Publish date
-
 In my last blog, we looked at five communication techniques that can help engage business managers in the work of cybersecurity.
In my last blog, we looked at five communication techniques that can help engage business managers in the work of cybersecurity. -
Making it real—harnessing data gravity to build the next gen SOC
In this post we address the question: “How do we make data gravity a reality in the security operations center (SOC) while we are under increased and constant pressure from motivated threat actors?” -
Delivering security innovation that puts Microsoft’s experience to work for you
Cybersecurity is the central challenge of our digital age. -
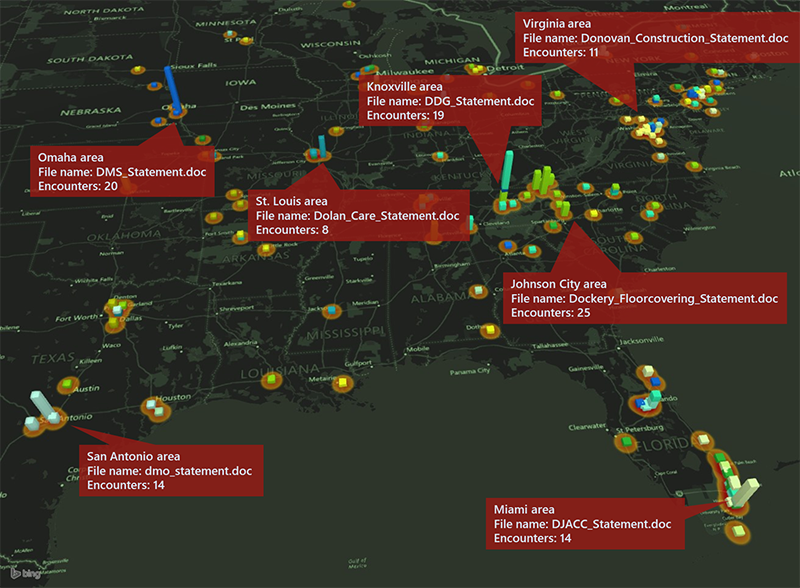
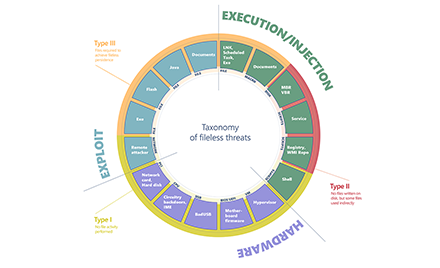
Small businesses targeted by highly localized Ursnif campaign
In social engineering attacks, is less really more? A new malware campaign puts that to the test by targeting home users and small businesses in specific US cities. -
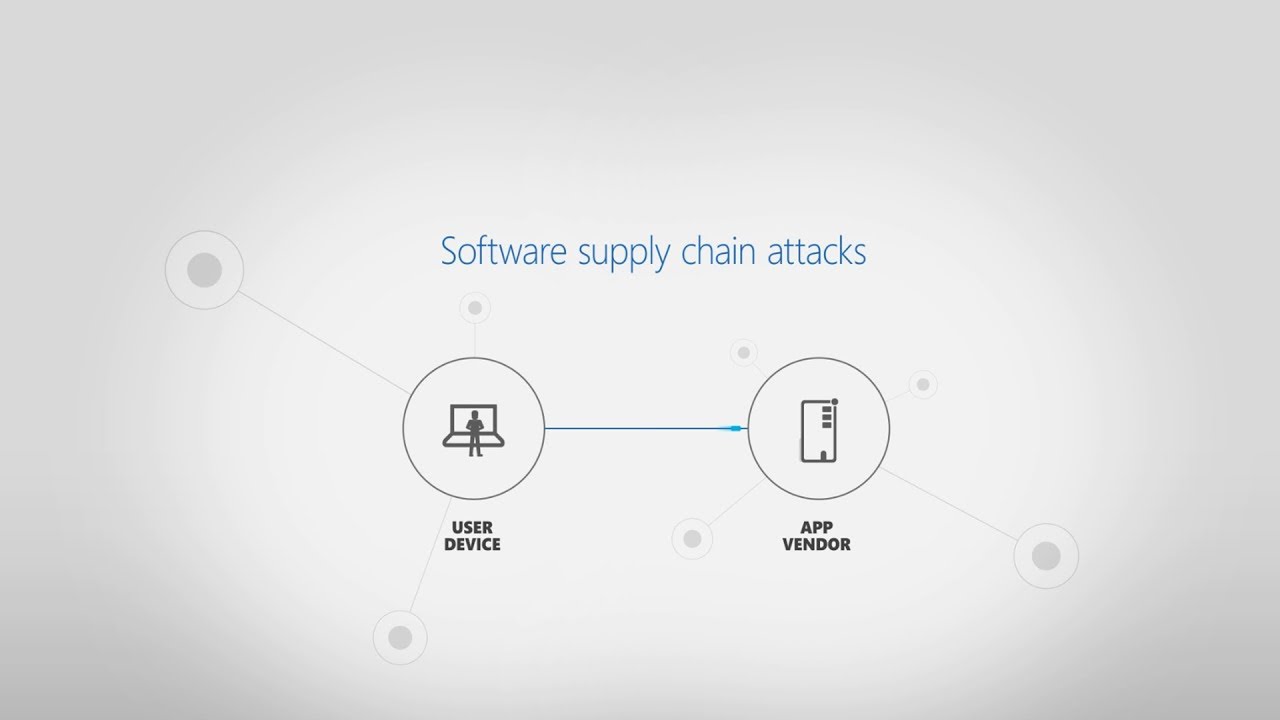
Attack inception: Compromised supply chain within a supply chain poses new risks
A new software supply chain attack unearthed by Windows Defender Advanced Threat Protection (Windows Defender ATP) emerged as an unusual multi-tier case. -

Assessing Microsoft 365 security solutions using the NIST Cybersecurity Framework
Microsoft 365 security solutions are designed to help you empower your users to do their best work securely, from anywhere and with the tools they love. -
Securing the modern workplace with Microsoft 365 threat protection – part 4
This post is authored by Debraj Ghosh, Senior Product Marketing Manager, Microsoft 365 Security. -
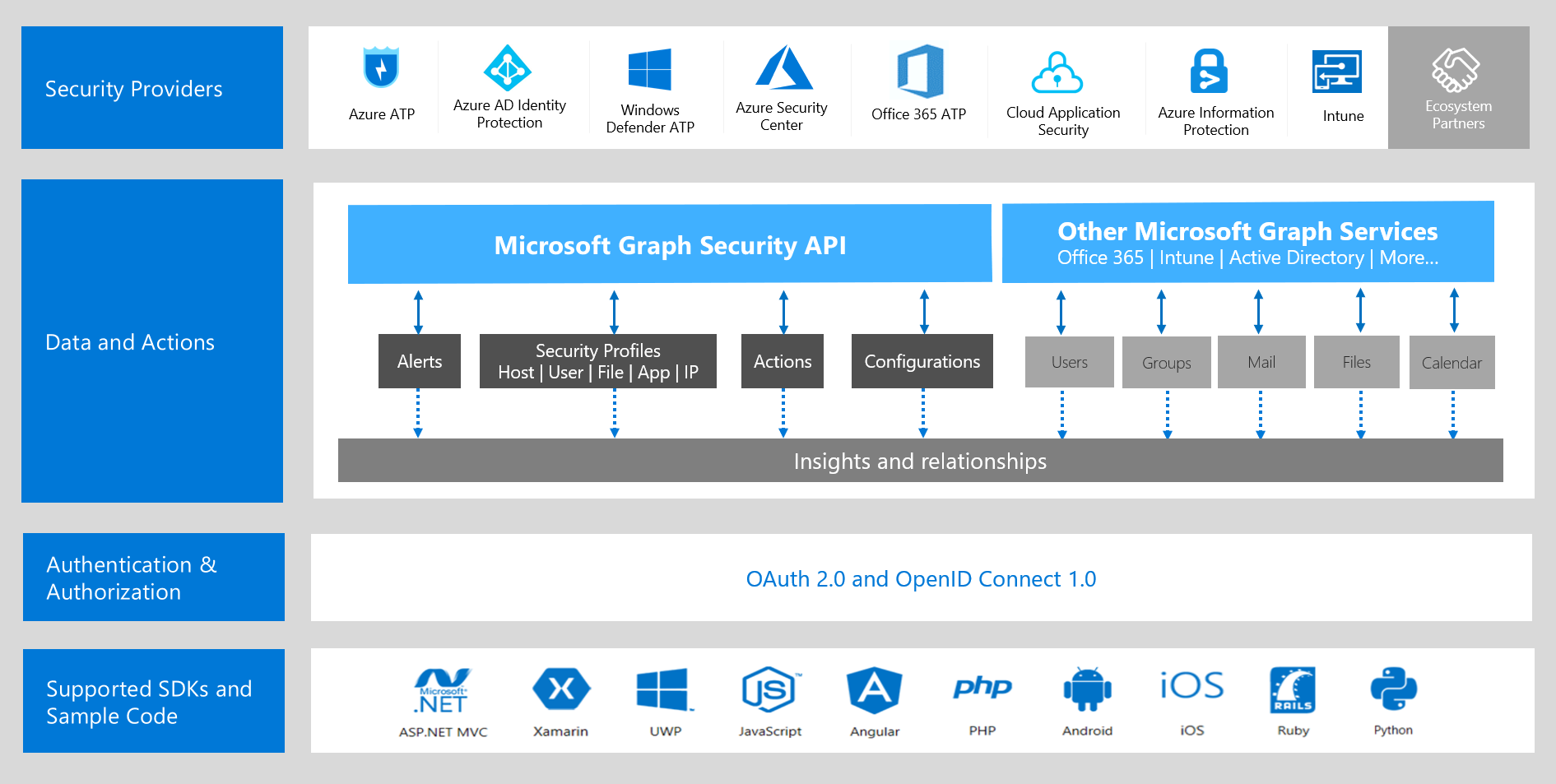
Connect to the Intelligent Security Graph using a new API
Most organizations deal with high volumes of security data and have dozens of security solutions in their enterprise, making the task of integrating various products and services daunting and complex. -
Poisoned peer-to-peer app kicked off Dofoil coin miner outbreak
On March 7, we reported that a massive Dofoil campaign attempted to install malicious cryptocurrency miners on hundreds of thousands of computers. -
How Office 365 protects your organization from modern phishing campaigns
This post is authored by Debraj Ghosh, Senior Product Marketing Manager, Microsoft 365 Security. -
How to mitigate rapid cyberattacks such as Petya and WannaCrypt
Because of how critical security hygiene issues have become and how challenging it is for organizations to follow the guidance and the multiple recommended practices, Microsoft is taking a fresh approach to solving them.