

Incident response
Incident response is the process of detecting, investigating, and responding to cyberattacks, security breaches, or IT incidents. Explore the latest trends and intelligence-driven strategies that help you prevent future attacks.
Refine results
Topic
Products and services
Publish date
-
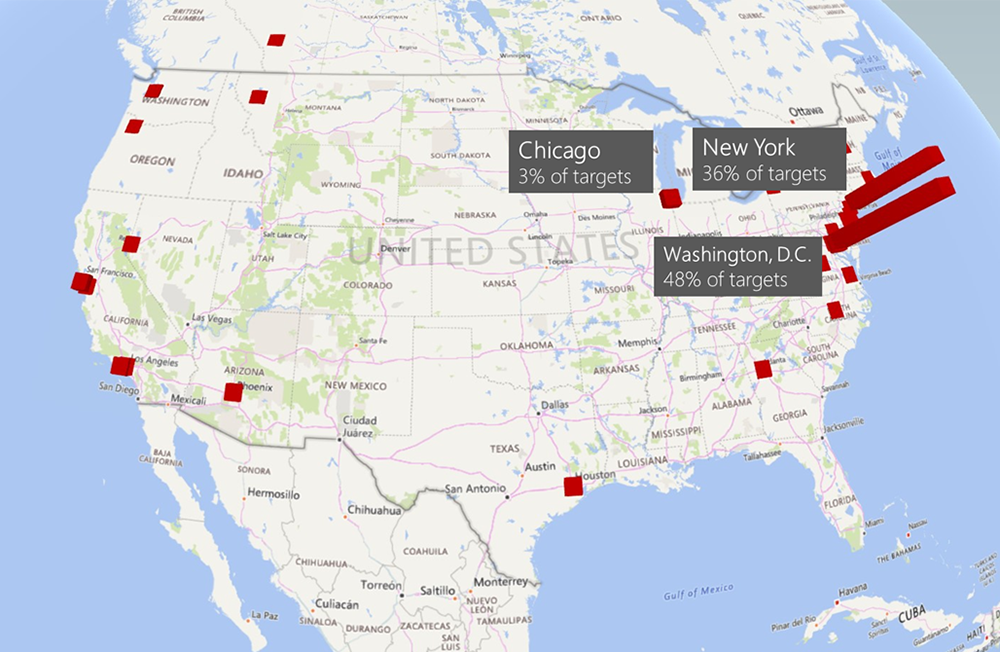
 Reuters recently reported a hacking campaign focused on a wide range of targets across the globe.
Reuters recently reported a hacking campaign focused on a wide range of targets across the globe. -

Insights from the MITRE ATT&CK-based evaluation of Windows Defender ATP
In MITRE’s evaluation of endpoint detection and response solutions, Windows Defender Advanced Threat Protection demonstrated industry-leading optics and detection capabilities. -

The evolution of Microsoft Threat Protection, January update
Learn about the top feature updates for Microsoft Threat Protection in January. -

Step 3. Protect your identities: top 10 actions to secure your environment
The “Top 10 actions to secure your environment” series outlines fundamental steps you can take with your investment in Microsoft 365 security solutions. -
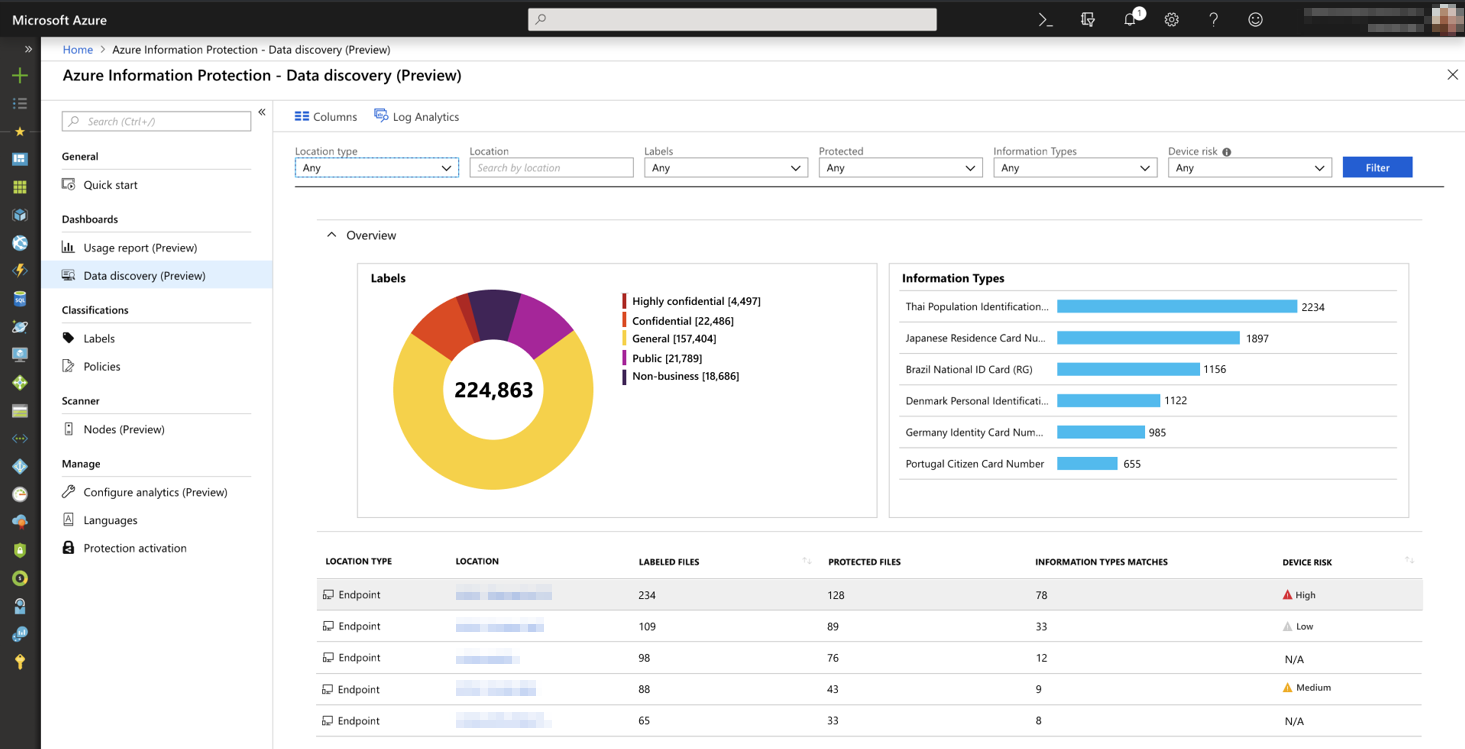
Microsoft Defender ATP integrates with Microsoft Information Protection to discover, protect, and monitor sensitive data on Windows devices
Microsoft Defender ATP, Microsoft’s endpoint protection platform, addresses this challenge by integrating with Azure Information Protection, Microsoft’s data classification, labeling, and protection solution. -

The evolution of Microsoft Threat Protection, February update
Learn about the latest enhancements to Microsoft Threat Protection, the premier solution for securing the modern workplace across identities, endpoints, user data, apps, and infrastructure. -

CISO Series: Lessons learned from the Microsoft SOC—Part 1: Organization
In the first of our three part series, we provide tips on how to manage a security operations center (SOC) to be more responsive, effective, and collaborative. -

DART: the Microsoft cybersecurity team we hope you never meet
Meet Microsoft’s Detection and Response Team (DART) and read their advice that may help you avoid working with them in future. -

4 tried-and-true prevention strategies for enterprise-level security
Learn about the four cyber hygiene best practices recommended in the 24th edition of the Microsoft Security Intelligence Report (SIR) to help reduce your risk of attack. -

CISO Series: Lessons learned from the Microsoft SOC Part 2b: Career paths and readiness
In our second post about people—our most valuable resource in the SOC—we talk about our investments into readiness programs, career paths, and recruiting for success. -

How to recover from a security breach
Actionable tips from security experts on how to prevent, mitigate, or recover from a cyberattack. -

Facing the cold chills
DART recently worked with a customer who had been subject to a targeted compromise where the entity was intently and purposefully attempting to get into their systems.





