A new best practice to protect technology supply chain integrity
The success of digital transformation ultimately relies on trust in the security and integrity of information and communications technology (ICT).


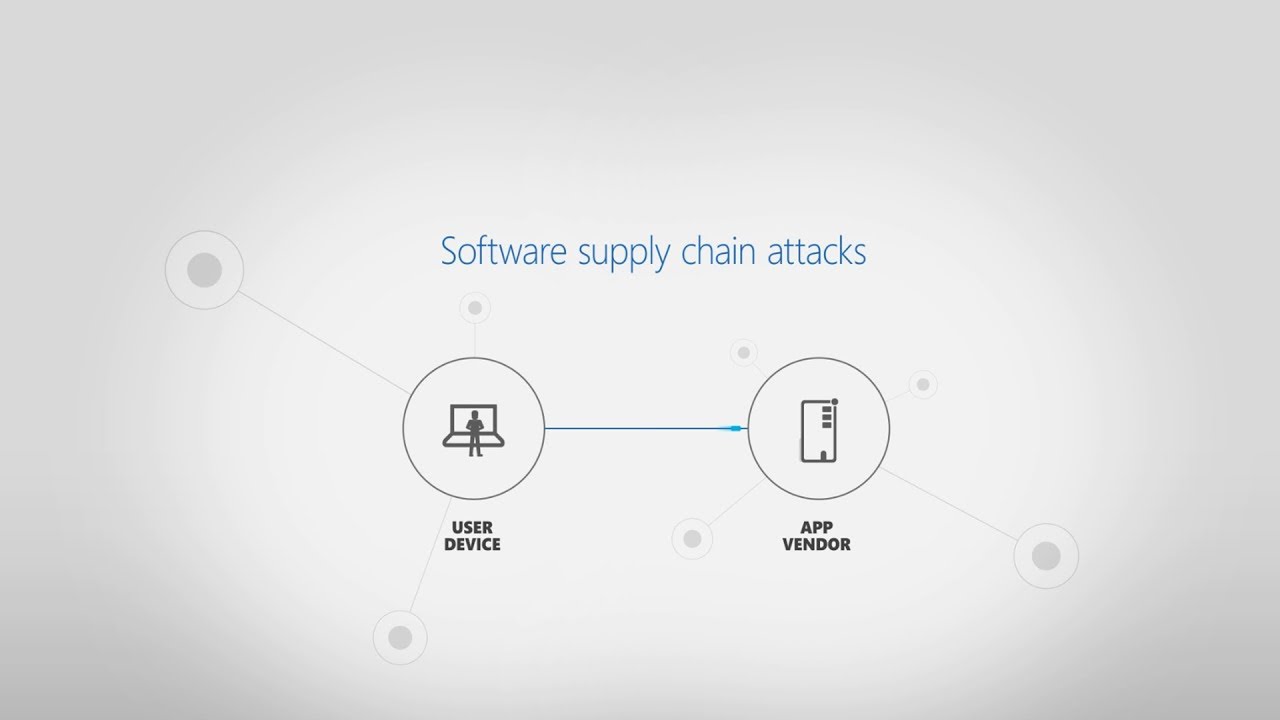
Supply chain attacks target software developers and suppliers with the goal of accessing source codes, building processes, or updating mechanisms. Explore how attackers exploit weaknesses to compromise trusted systems and distribute malicious code.