Cyberattacker techniques, tools, and infrastructure
Cyberattackers constantly evolve their techniques, tools, and infrastructure to launch increasingly complex attacks. Learn about the latest tactics and how to detect, disrupt, and defend against them.
Refine results
Topic
Products and services
Publish date
-
 DART offers steps you can take to protect your network from BlueKeep, the “wormable” vulnerability that can create a large-scale outbreak due to its ability to replicate and propagate.
DART offers steps you can take to protect your network from BlueKeep, the “wormable” vulnerability that can create a large-scale outbreak due to its ability to replicate and propagate. -

Bring your own LOLBin: Multi-stage, fileless Nodersok campaign delivers rare Node.js-based malware
A new fileless malware campaign we dubbed Nodersok delivers two very unusual LOLBins to turn infected machines into zombie proxies. -
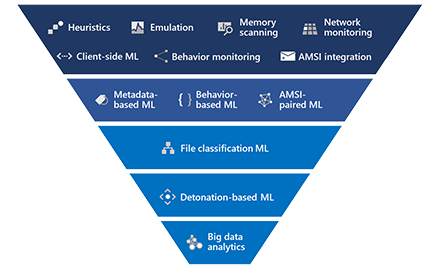
In hot pursuit of elusive threats: AI-driven behavior-based blocking stops attacks in their tracks
Two new machine learning protection features within the behavioral blocking and containment capabilities in Microsoft Defender ATP specialize in detecting threats by analyzing behavior, adding new layers of protection after an attack has started running. -

GALLIUM: Targeting global telecom
Microsoft Threat Intelligence Center (MSTIC) is raising awareness of the ongoing activity by a group we call GALLIUM, targeting telecommunication providers. -
Multi-stage downloader Trojan sLoad abuses BITS almost exclusively for malicious activities
Many of today’s threats evolve to incorporate as many living-off-the-land techniques as possible into the attack chain. -

Data science for cybersecurity: A probabilistic time series model for detecting RDP inbound brute force attacks
Microsoft Defender ATP data scientists and threat hunters collaborate to use a data science-driven approach to detecting RDP brute force attacks to protect customers against real-world threats. -

sLoad launches version 2.0, Starslord
sLoad has launched version 2.0. With the new version, sLoad, which is a PowerShell-based Trojan downloader notable for its almost exclusive use of the Windows BITS service for malicious activities, has added an anti-analysis trick and the ability to track the stage of infection for every affected machine. -

Ghost in the shell: Investigating web shell attacks
Web shell attacks allow adversaries to run commands and steal data from an Internet-facing server or use the server as launch pad for further attacks against the affected organization. -

Behavioral blocking and containment: Transforming optics into protection
Behavioral blocking and containment capabilities leverage multiple Microsoft Defender ATP components and features to immediately stop attacks before they can progress. -

Latest Astaroth living-off-the-land attacks are even more invisible but not less observable
Astaroth is back sporting significant changes. -

Inside Microsoft 365 Defender: Mapping attack chains from cloud to endpoint
In the first blog in the Inside Microsoft Threat Protection series, we will show how MTP provides unparalleled end-to-end visibility into the activities of nation-state level attacks like HOLMIUM. -

Defending Exchange servers under attack
Exchange servers are high-value targets.