

Cyberattacker techniques, tools, and infrastructure
Cyberattackers constantly evolve their techniques, tools, and infrastructure to launch increasingly complex attacks. Learn about the latest tactics and how to detect, disrupt, and defend against them.
Refine results
Topic
Products and services
Publish date
-
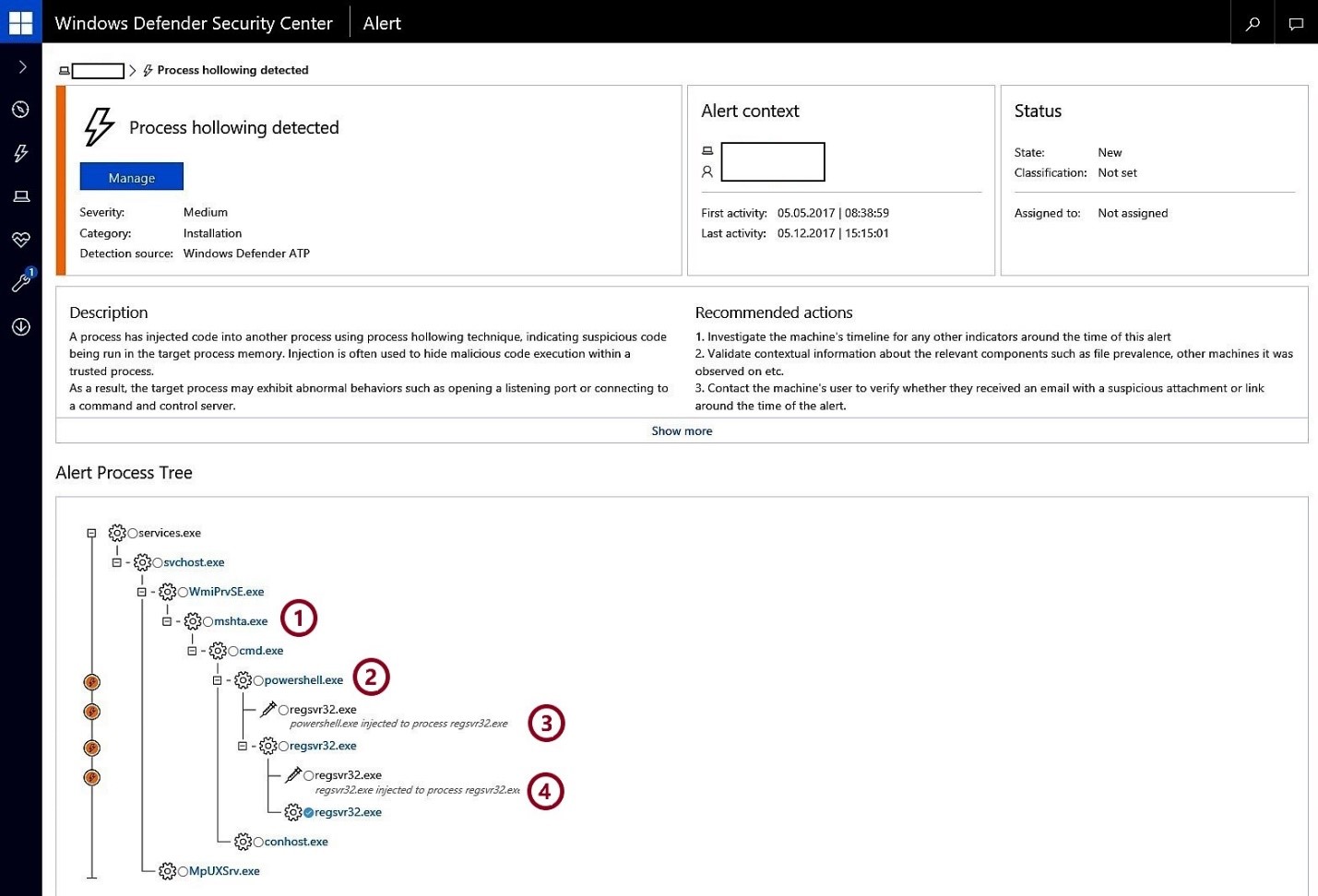
 Advanced cyberattacks emphasize stealth and persistence: the longer they stay under the radar, the more they can move laterally, exfiltrate data, and cause damage.
Advanced cyberattacks emphasize stealth and persistence: the longer they stay under the radar, the more they can move laterally, exfiltrate data, and cause damage. -
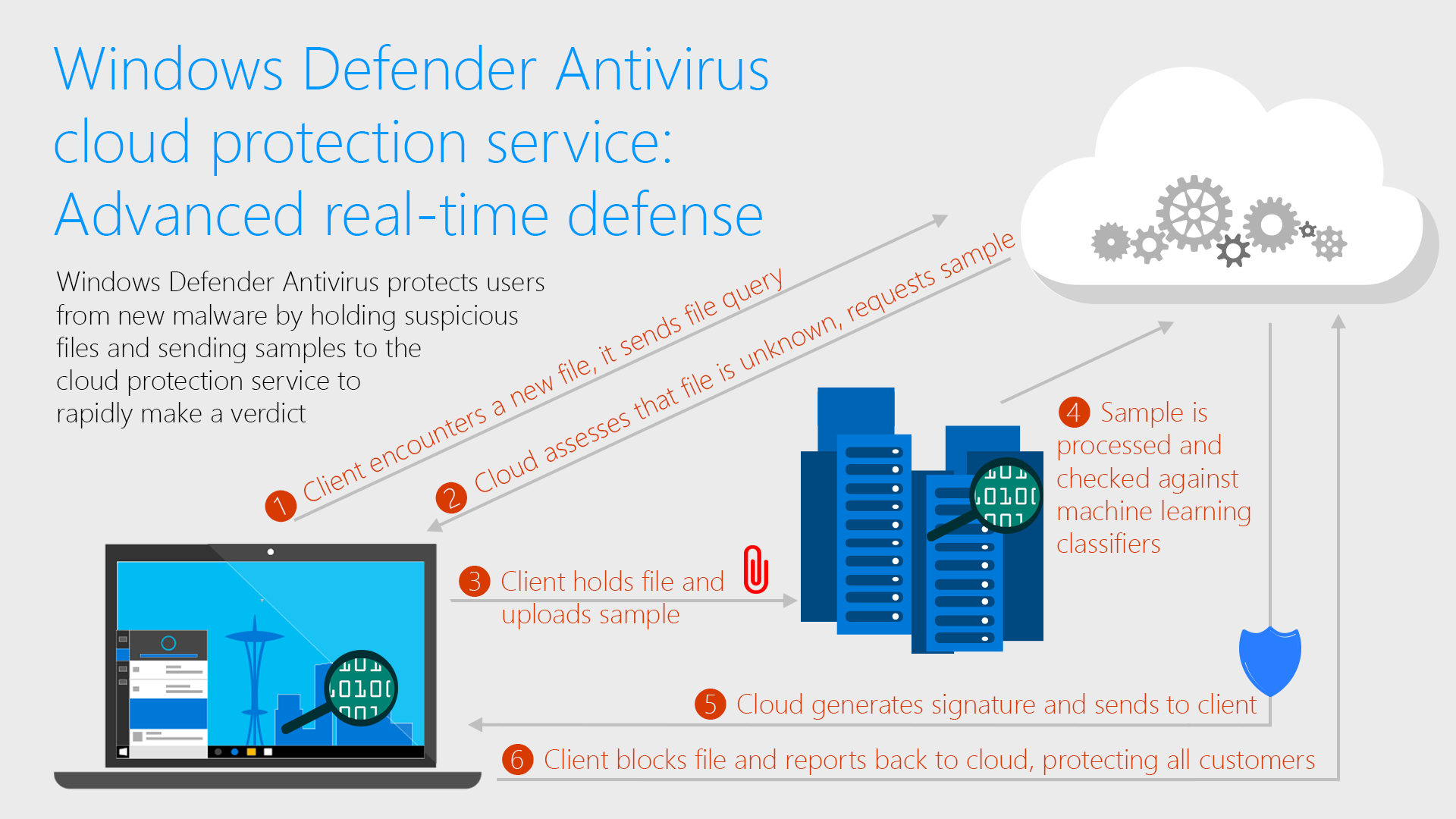
Windows Defender Antivirus cloud protection service: Advanced real-time defense against never-before-seen malware
For cybercriminals, speed is the name of the game. -
Windows Defender ATP machine learning: Detecting new and unusual breach activity
Microsoft has been investing heavily in next-generation security technologies. -

New tech support scam launches communication or phone call app
(Note: Our Tech support scams FAQ page has the latest info on this type of threat, including scammer tactics, fake error messages, and the latest scammer hotlines. -
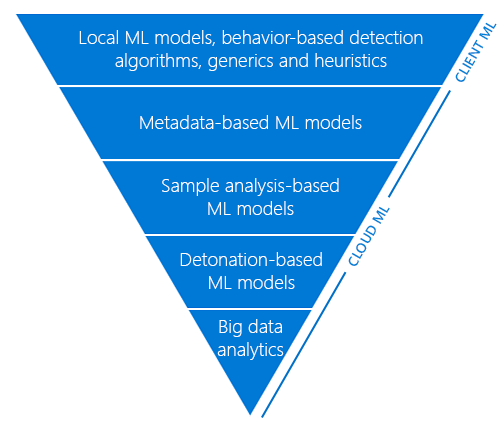
Detonating a bad rabbit: Windows Defender Antivirus and layered machine learning defenses
Windows Defender Antivirus uses a layered approach to protection: tiers of advanced automation and machine learning models evaluate files in order to reach a verdict on suspected malware. -
How Microsoft tools and partners support GDPR compliance
There are tools available that can ease kick-off activities for CISOs, CIOs, and DPOs. -

Now you see me: Exposing fileless malware
Attackers are determined to circumvent security defenses using increasingly sophisticated techniques. -

Protecting customers from being intimidated into making an unnecessary purchase
Protecting the modern workplace from a wide range of undesirable softwareOur evaluation criteria describe the characteristics and behavior of malware and potentially unwanted applications and guide the proper identification of threats. -
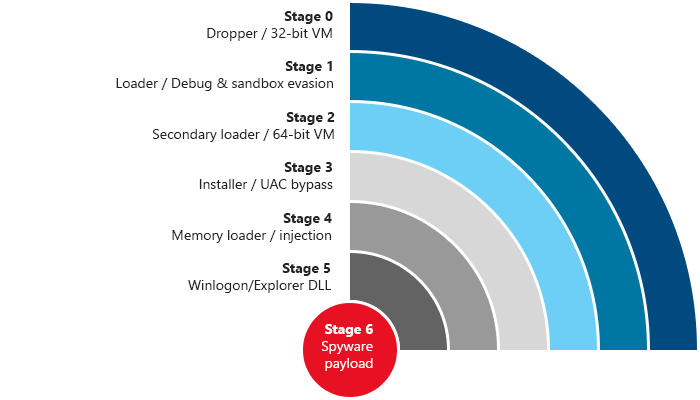
FinFisher exposed: A researcher’s tale of defeating traps, tricks, and complex virtual machines
Office 365 Advanced Threat Protection (Office 365 ATP) blocked many notable zero-day exploits in 2017. -
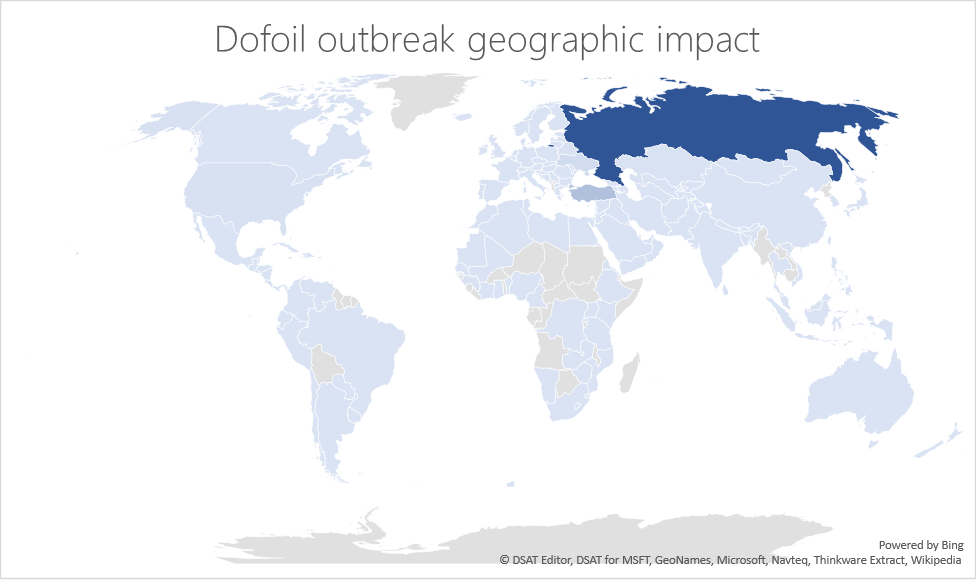
Behavior monitoring combined with machine learning spoils a massive Dofoil coin mining campaign
Update: Further analysis of this campaign points to a poisoned update for a peer-to-peer (P2P) application. -

Invisible resource thieves: The increasing threat of cryptocurrency miners
The surge in Bitcoin prices has driven widescale interest in cryptocurrencies. -
Poisoned peer-to-peer app kicked off Dofoil coin miner outbreak
On March 7, we reported that a massive Dofoil campaign attempted to install malicious cryptocurrency miners on hundreds of thousands of computers.





