
Computer security updates, commonly referred to as “patches,” are a crucial aspect of the IT operations of every large organization today. As a global software company with more than 230,000 employees worldwide, we at Microsoft are no different.
Like most aspects of our IT services journey, our security and patch management story is deeply connected with cloud computing, automation, and, most recently, AI technology. It’s a story that embraces continuous improvement and innovations that are saving our IT admins and users time and hassle while deterring attacks and enhancing security across the organization.
With the development of services like Windows Update client policies (formerly known as Windows Update for Business), Azure Update Manager, and Intune Enterprise Application Management, we’re leading the way in offering best-of-breed security solutions that help organizations stay compliant and safe in an increasingly perilous digital world.
The growing threat landscape
As the developer and provider of Windows, Microsoft 365, Microsoft Azure cloud services, and other widely used software technologies, we’re in a unique position to influence and protect the computer systems used by billions of people around the world. And these systems have never been under greater threat by bad actors and cybercriminals than they are today.

“Our customers face more than 600 million cybercriminal and nation-state attacks every day, ranging from ransomware to phishing to identity attacks,” states our 2024 Digital Defense Report. “Microsoft’s unique, expansive, and global vantage point gives us unprecedented insight into key trends in cybersecurity affecting everyone from individuals to nations.”
The report also notes that we’ve made digital security our top corporate priority, with more than 34,000 dedicated security engineers across the company.
“The malign actors of the world are becoming better resourced and better prepared, with increasingly sophisticated tactics, techniques, and tools that challenge even the world’s best cybersecurity defenders,” Tom Burt, corporate vice president of customer security and trust, says in the report. “We all can, and must, do better, hardening our digital domains to protect our networks, data, and people at all levels.”
With such an unprecedented number of threats, one of our major priorities at Microsoft Digital, the company’s IT organization, is making sure our global network infrastructure and the more than 750,000 devices accessing our network are always up to date and compliant with the latest software patches. As Customer Zero for our software products, we strive to remain on the cutting edge of the latest cybersecurity innovations. That means taking advantage of the latest Microsoft tools and processes on server-side and client-side patching.
The world as it was: On-premises IT and manual updates
A decade or so ago, much of the world’s computer networks were still being run primarily via on-premises servers and other onsite hardware. Maintaining these systems mostly relied on manual updates by IT administrators, which was a huge drain on time and resources.
“Our patch-management systems back then included Microsoft System Center Configuration Manager (SCCM) and Windows Server Update Services,” says Senthil Selvaraj, a principal group project manager at Microsoft Digital. “We were doing everything on-premises, managed within the Microsoft tenant onsite.”
Patching product history at Microsoft
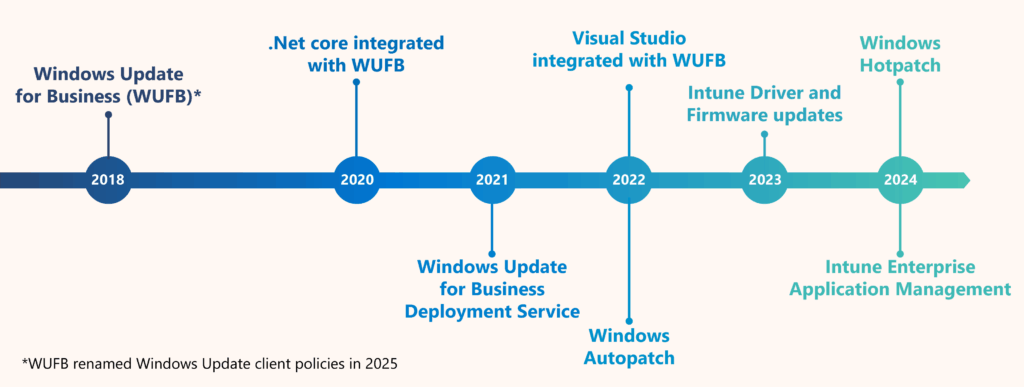
This meant that simply downloading and installing the routine security patches that were released each month was a major task for the company’s thousands of IT admins.
“The admins used to have to download the updates, validate them, approve them, and then push them out to devices,” says Harshitha Digumarthi, a senior product manager with Microsoft Digital. “It used to take a considerable amount of time each month for these processes. There was no proper automation in place.”
As the IT world shifted to cloud solutions and more modern software management approaches, the patching process needed to shift with it, Selveraj notes.
“As we moved everything to the cloud, we leveraged modern Microsoft tools such as Intune, OneDrive for Business, SharePoint, etc.,” he says. “And we were also helping our customers move through that process as well. This is in keeping with the overall Microsoft vision of continuous improvement.”
The journey to modern patch management on Windows
In 2018, we introduced Windows Update for Business (WUFB), a major milestone on the patch management migration journey. The service is now called Windows Update client policies.
Of course, like any story of technological progress, nothing happens overnight or in a straight line. As Digumarthi explains, we in Microsoft Digital went through a patch management transition phase, marked by a hybrid systems approach.
“We didn’t immediately shift everything from SCCM to Windows Update for Business and Microsoft Intune,” she says. “There is transitionary stage—known as hybrid AD—where the client devices still have SCCM on them, with Intune running parallel on those devices.”
WUFB ushered in a more efficient and modern approach to patch management.
“It’s an automated, intelligent service which can identify what updates the device needs, find the applicable updates, and automatically push those updates onto the devices,” Digumarthi says.
She notes that IT admins at other organizations might push these updates out to their devices in phases, often called deployment rings. But at Microsoft, we do them all at once for the entire company, in a program popularly called Patch Tuesday.
“We have established programs to pre-validate updates, allowing us to deploy them automatically and simultaneously across all devices, significantly accelerating compliance,” Digumarthi says.
This control is enabled through Windows Update policies, which allow administrators to manage key actions such as reboot timing. As a result, vulnerabilities are addressed quickly, and all devices are brought into compliance with the latest secure Windows updates.
After establishing a more efficient approach to Windows security patching, we rolled out WUFB Deployment Services in 2021. This process, which brought similar gains in efficiency and automation, handles new Windows features, which are typically released on six-month cycles.
According to Digumarthi, a major challenge to patch management for Windows is the number of different versions, including the .Net Framework, .Net Core, Visual Studio, Visual Studio Code, SQL, and more. Over the last few years, we have developed a unified internal-to-Microsoft patching solution to handle all of these various updates.
“These are extremely different streams, so we’ve worked closely with these product groups to bring them all into one update, which we call the unified update,” Digumarthi says. “This way, the IT admin doesn’t need to deploy all these different updates individually. It’s also completely automated, so it’s much easier for both admins and users to stay up to date and compliant. It’s a huge achievement.”
Other important patch automation issues are firmware and driver updates. These updates used to be deployed manually by admins every month, but that changed in 2024.
“We now have a new feature, in partnership with Windows and the Intune team, called the Intune Driver and Firmware updates,” Digumarthi says. “It gives admins a portal where they can simply click a button and approve whatever the latest firmware and driver updates are; no need to manually download, package, and deploy the updates. It’s easier for them to understand, and we’ve seen great patch compliance improvement in this area.”
Patch management on the server side
While Windows Update client policies handles the client-side updates for the more than 750,000 devices on our corporate network, we also needed a modern solution for patch management on our roughly 50,000 network servers.
Keeping network servers compliant with the latest security updates is extremely important.
“We must proactively safeguard our development environments,” says Humberto Arias, senior product manager in Microsoft Digital. “When vulnerabilities are exploited by malicious actors, even a single compromised bug can cascade rapidly, potentially impacting millions of users. Anticipating and mitigating these risks early is essential to maintaining trust and security.”
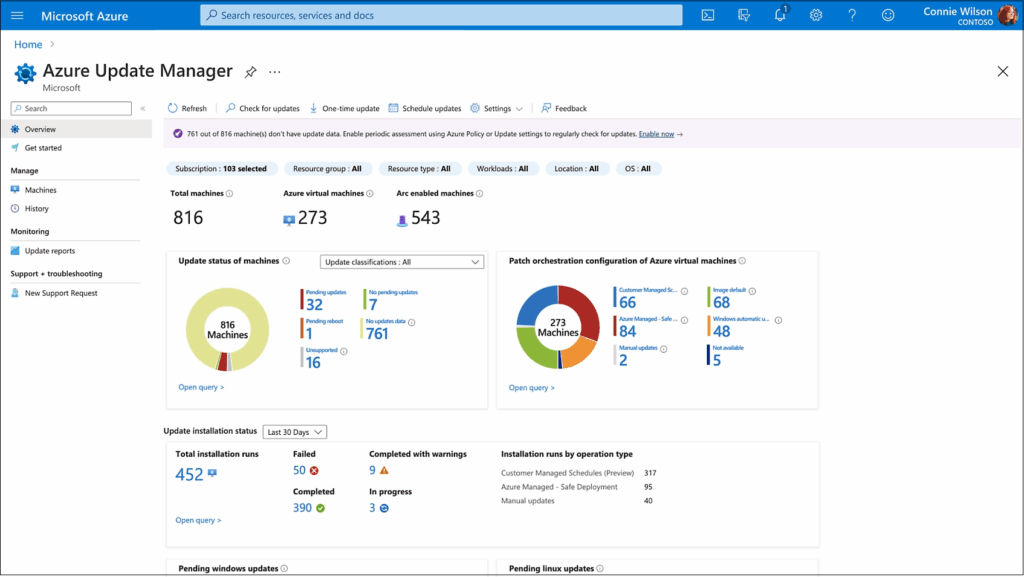
The solution is Azure Update Manager (AUM), a product that enables network administrators to deploy and manage all their server security update packages in one stream. AUM also supports hybrid (on-premises and cloud) network environments, which is a competitive advantage.
“A lot of customers like the flexibility and redundancy of multi-cloud environments,” Arias says. “AUM is our one-stop solution for patching all your servers, regardless of where they reside—on-premises, in the cloud, or in hybrid environments. It’s a great advantage of using AUM.”
Patching with Azure Update Manager
The challenge of patching non-Windows devices
Microsoft believes in empowering our employees to do their job on the device that works best for them (sometimes called Bring Your Own Device, or BYOD). But that policy opens up the challenge of making sure all those devices meet our security standards, including those running on the MacOS, iOS, and Android platforms.
“People do a lot more work on their mobile devices than they used to; we have about 80,000 Android devices and about 150,000 iOS devices that our employees connect to our network with,” says John Philpott, a senior product manager in Microsoft Digital. “We need to make sure that all these devices have the latest OS security patches, or it puts our network at risk.”
The tricky part is that because Microsoft doesn’t make the operating systems, we can’t consistently manage the device environment or the patches themselves. Instead, the common approach in this situation is to make sure that employees know about the latest patches for their device and enforce compliance by controlling their access to the Microsoft corporate network. Getting employees to voluntarily keep their devices up to date is critically important.
The frequency and requirements for installing the updates depends on the platform.
“For Android, how often your phone is updated varies, depending on the manufacturer and model; this makes developing a consistent patching experience a challenge,” Philpott says. “It’s a balancing act, but we’ve gradually tightened our patch requirements and are educating employees on the best Android devices to choose to meet patching requirements.
Patch enforcement for Apple devices is much tighter, according to Philpott.
“If there’s a security threat, Apple will quickly make a patch available,” he says. “We have a standard process of enforcing compliance within 14 days. We tell our users that if they haven’t installed the update after 12 days, we’ll install the patch and enforce a reboot. If the device has not been patched after 14 days, we’ll remove their network access.”
The other area of mobile device patching that has received increased scrutiny in recent years is applications, both our first-party apps and third-party apps. We work closely with the Microsoft Intune product group to make sure that these apps are patched as frequently as possible.
“We do a lot of discussions with the Intune team about how we can enforce these updates,” Philpott says. “We want to make sure all the Microsoft apps are up to date on mobile, but we’re also making a big push to enforce third-party app patching as well. If someone exploits an app like Adobe Acrobat that can be a threat to our security, so we want users running the latest versions of all the major apps.”
Autopatch and hotpatching

Our patch management journey is one of helping develop solutions that automate security and feature updates as much as possible, reducing the strain on IT resources. As part of these efforts, we work closely with the Microsoft product groups as Customer Zero for their update offerings. One prominent step on this journey was the introduction of Windows Autopatch in 2022.
Windows Autopatch is a cloud service for enterprise customers that automates the updates to Windows, Microsoft 365, Microsoft Edge, and Microsoft Teams. It also offers greater control for patching different groups of devices on different schedules.
“Autopatch offers admins a single-pane view where they can manage the patches across their organization, from the same perspective,” says Katie Yao, a senior product manager on the Autopatch team. “And with Autopatch Groups, they can dynamically assign users to different groups, which gives them a lot of flexibility on how and when devices are updated.”
Another innovation that the Autopatch service offers is hotpatching. This feature helps IT teams keep devices secure without the usual disruption of monthly reboots. Security updates are applied immediately in the background. This means fewer interruptions for users and less coordination effort for admins—especially in environments where uptime is critical.
For IT admins managing a large volume of devices, this is a big win. Hotpatching reduces the amount of time it takes to achieve security compliance across the whole environment, with no delays or deferrals.
“Customers were telling us that rebooting all devices every month was too much in some cases,” Yao explains. “So, we’ve moved to a process where they get the updates every month, but they only need to reboot the machines once every three months. This way they get the latest security and feature updates, but they don’t need to reboot their devices as often.”
The future of patch management
Our patch management story continues to evolve as we apply the latest tools and technologies to our processes at Microsoft Digital. We see great opportunities for industry-wide improvements, such as with application patching.
“The Intune Enterprise Application Management solution is a huge opportunity for us,” Selvaraj says. “Right now, there’s a gap in how applications are managed across large organizations—are they healthy? Are they vulnerable? Are they up to date? We hope that this solution will address these needs.”
Of course, just as with many aspects of today’s software development, the future of patching will be greatly impacted by AI innovations.
“AI tools are the next stage in our continuous improvement process for patch management,” Selvaraj notes. “We’re currently working on a new solution called Device Care, which is a tool that leverages AI to monitor, predict, and resolve device and infrastructure issues for admins and employees. Another AI tool in this space is Microsoft Security Copilot, which helps with daily security operations.”
And as the computer security landscape evolves, with more frequent and more sophisticated attacks coming every day, we’ll continue to refine and develop our patching tools and strategies. It’s the only way to ensure that our networks and devices—and those of our customers—remain as secure as possible.

Here are some tips to help guide your own organization’s patch management approach:
- Stay alert to risk. The rapidly increasing size and scale of the cybersecurity threat landscape has intensified the need for more sophisticated patching solutions.
- Educate your employees. Making sure that everyone in your organization is aware of the importance of keeping devices up to date with the latest patches is a key part of your overall security strategy.
- Save time and resources with automated updates. Windows Update client policies (formerly WUFB) offers automated patching, which can greatly reduce the amount of time your IT admins must spend identifying, configuring, and deploying updates.
- Update your infrastructure where it lives. Azure Update Manager provides a powerful, flexible patching solution that works for on-cloud, on-premises, and hybrid network infrastructures.
- Adapt to a flexible device environment. Mobile-device patching can be a complex challenge, especially if your organization embraces a Bring Your Own Device philosophy. Services like Microsoft Intune can ensure that devices are well-managed and kept up to date on the latest security fixes.
- Maintain availability. If you have critical servers and devices that you don’t want to reboot every month, consider a hotpatching approach that keeps your devices updated without rebooting.
- Take advantage of intelligent patching solutions. AI advances promise even greater innovation to come in the patching space, including services like Microsoft Device Care, Security Copilot, and Enterprise Application Management.

- Learn how we’re harnessing first-party patching technology at Microsoft.
- Check out how we’re approaching Windows patching at Microsoft.
- Read about our experience migrating from Microsoft Monitoring Agent to Microsoft Azure Arc and Azure Update Manager.
- Discover how we’re protecting Microsoft from ransomware attacks.
- Find out how we’re transitioning to modern access architecture with our Zero Trust principles.







