

Threat trends
Cybersecurity threats are always changing. Explore the latest trends—and learn how to stay ahead of them.
Refine results
Topic
Products and services
Publish date
-
Currently three exploits have been demonstrated as technically possible.
-
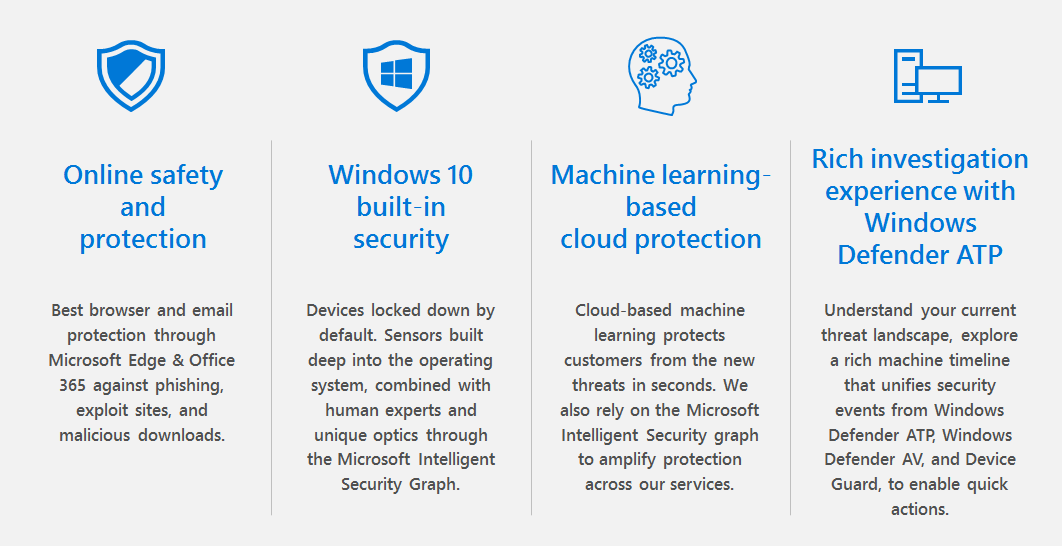
Ransomware 1H 2017 review: Global outbreaks reinforce the value of security hygiene
The trend towards increasingly sophisticated malware behavior, highlighted by the use of exploits and other attack vectors, makes older platforms so much more susceptible to ransomware attacks. -

Tips for securing your identity against cybersecurity threats
This post is authored by Simon Pope, Principal Security Group Manager, Microsoft Security Response Center. -
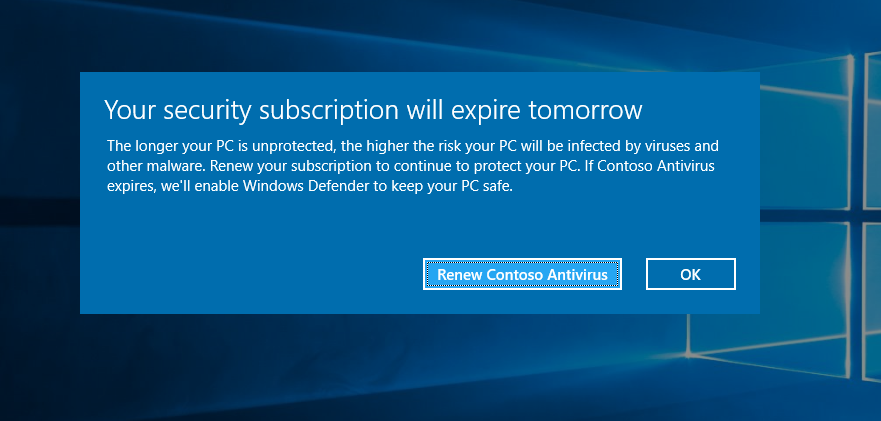
Partnering with the AV ecosystem to protect our Windows 10 customers
On Friday May 12th, and for several days afterwards, more than a quarter-million computers around the world fell victim to the ransomware known as WannaCrypt or WannaCry. -
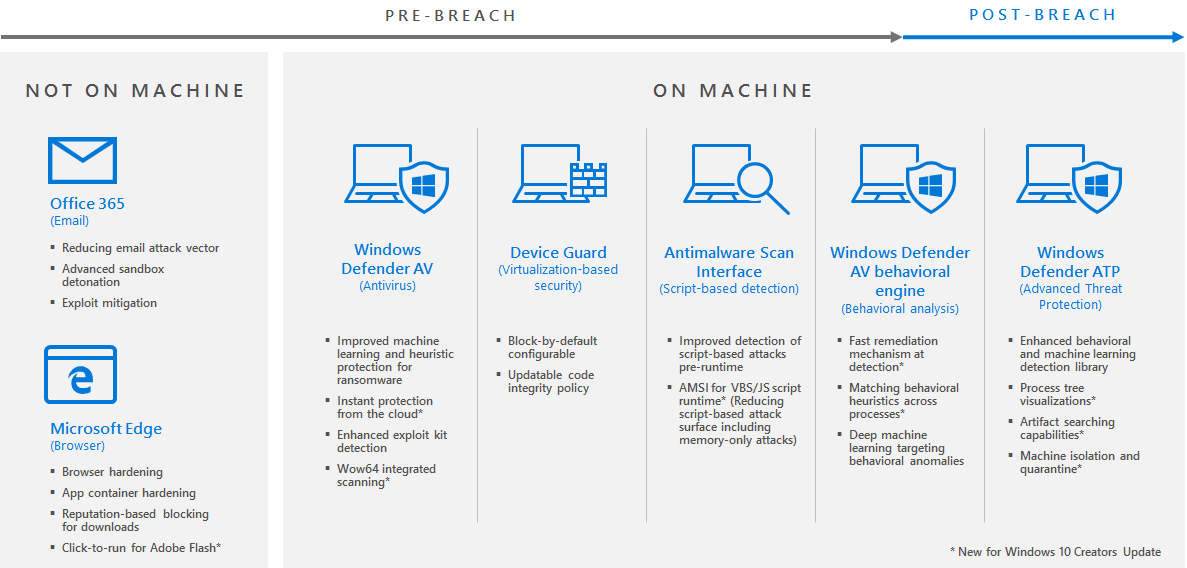
Windows 10 Creators Update provides next-gen ransomware protection
Multiple high-profile incidents have demonstrated that ransomware can have catastrophic effects on all of us. -
Cybersecurity’s perfect storm
The unprecedented scale and sophistication of modern cyberthreats, combined with the rapidly disappearing IT perimeter, means that while preventing an attack from becoming a breach is ideal, it is no longer realistic. -
Our commitment to our customers’ security
Windows is the only platform with a customer commitment to investigate reported security issues and proactively update impacted devices as soon as possible. -
Modern browsers are closing the door on Java exploits, but some threats remain
Was 2015 the year the industry finally eradicated Java exploitation? Well, not quite, but the good news is we’re getting there. -
The Emerging Era of Cyber Defense and Cybercrime
Cyber threats are everywhere, from hackers causing mischief to show off their skills to organized crime syndicates employing sophisticated financial ruses against governmental organizations, businesses, social channels and individuals. -
ABB Automation & Power World 2015 – Cybersecurity in the evolving threat landscape
In early March, I had the fortunate opportunity to speak at the ABB Automation & Power World 2015 conference in Houston, TX. -
KRBTGT Account Password Reset Scripts now available for customers
Although pass-the-hash credential theft and reuse attacks aren’t new, more recently security researchers have been focusing on attack methods for Kerberos authentication. -
Washington Post – A Time to Patch III: Apple
You’ve probably already read Brian Krebs article A Time to Patch III: Apple, but if you haven’t, I encourage you to read it and read the various responses he received – the responses run the gamut of Linux advocates (“You do understand that Mac OS X is not a version of Linux, and is not […]





