


Information protection and governance
Information protection and governance involves safeguarding sensitive data and managing its lifecycle to ensure compliance and reduce risk. earn about strategies and solutions that’ll help you safeguard your data.
Refine results
Topic
Products and services
Publish date
-
 Five years ago, we started on a journey to update and simplify information protection at Microsoft.
Five years ago, we started on a journey to update and simplify information protection at Microsoft. -

Demystifying Password Hash Sync
We debunk the myths about Password Hash Sync (PHS) so you can gain security benefits by using the full capabilities of this service. -

Ovum recommends Microsoft security to safeguard your hybrid and multi cloud environments
Read why Ovum believes Microsoft 365 and Azure can protect enterprises who use multiple cloud providers. -

Defend your digital landscape with Microsoft 365
Detect a security breach in real-time and respond immediately to reduce damage. -

Forcepoint DLP integration with Microsoft Information Protection—protecting your critical data
Microsoft and Forcepoint are working closely to develop an integrated solution that makes it easy to discover, classify, label, and protect critical business data. -

Step 8. Protect your documents and email: top 10 actions to secure your environment
The “Top 10 actions to secure your environment” series outlines fundamental steps you can take with your investment in Microsoft 365 security solutions. -
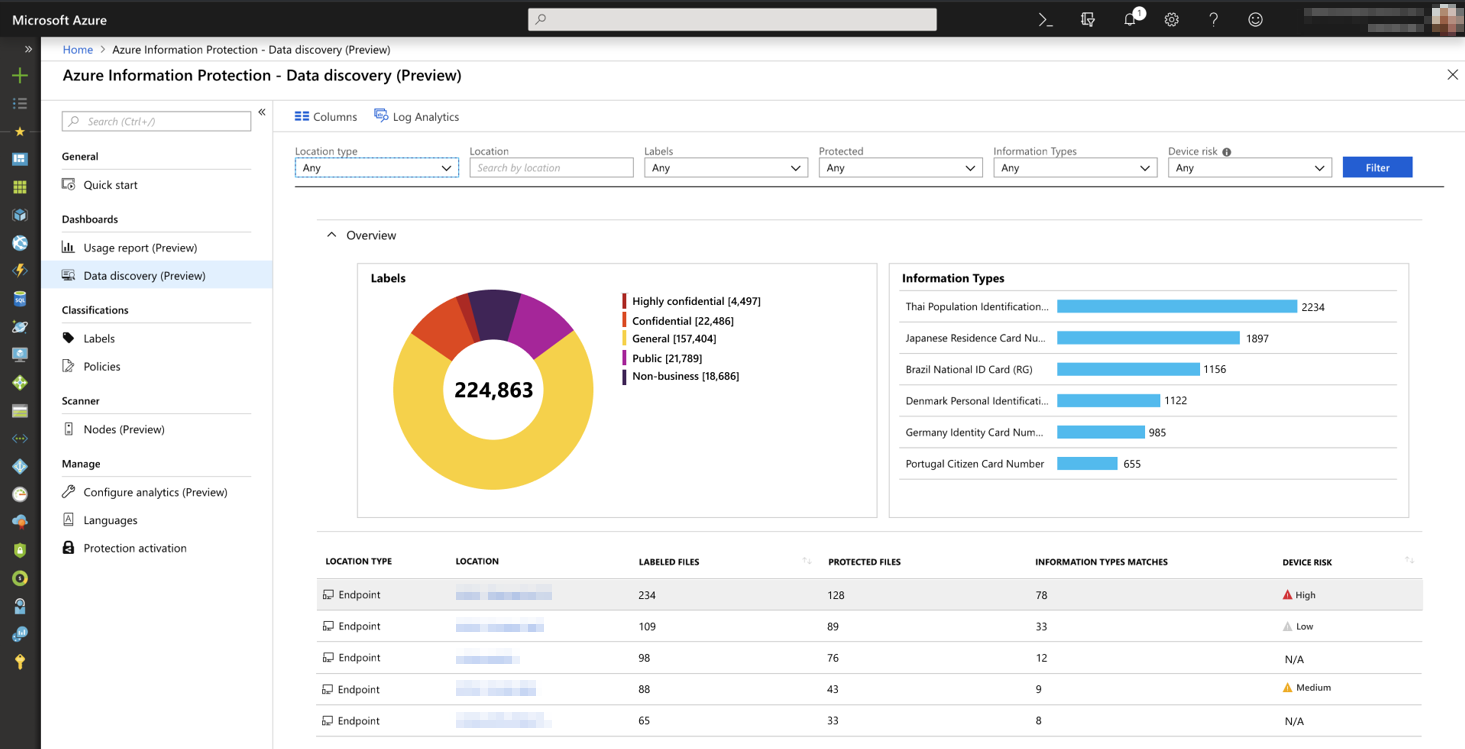
Microsoft Defender ATP integrates with Microsoft Information Protection to discover, protect, and monitor sensitive data on Windows devices
Microsoft Defender ATP, Microsoft’s endpoint protection platform, addresses this challenge by integrating with Azure Information Protection, Microsoft’s data classification, labeling, and protection solution. -
Use Windows Information Protection (WIP) to help make accidental data leakage a thing of the past
Windows Information Protection (WIP) is an out-of-the box data leakage prevention feature for Windows 10 that can automatically apply protection for work files and data to prevent accidental data leakage. -
Take these steps to stay safe from counterfeit software and fraudulent subscriptions
This post is authored by Matt Lundy, Assistant General Counsel, Microsoft. -

Microsoft offers several mechanisms to protect against ransomware
The start of a new year is the perfect time to reassess your security strategy and tactics – especially when looking back at the new levels of ransomware’s reach and damage in 2017. -

Tips for protecting your information and privacy against cybersecurity threats
This post is authored by Steven Meyers, security operations principal, Microsoft Cyber Defense Operations Center. -
Cybercrime and freedom of speech – A counterproductive entanglement
This post is authored by Gene Burrus, Assistant General Counsel.





