


Cloud security
Learn more about the solutions, procedures, policies, and controls that help you protect your cloud-based systems and data.
Refine results
Topic
Products and services
Publish date
-
 Recently, I hosted a Chief Information Security Officer roundtable in Washington, DC.
Recently, I hosted a Chief Information Security Officer roundtable in Washington, DC. -
4 steps to managing shadow IT
Shadow IT is on the rise. More than 80 percent of employees report using apps that weren’t sanctioned by IT. -

Stepping up protection with intelligent security
With digital transformation, technology becomes increasingly central to every business and organization. -

Cybersecurity in a modern age
By 2021, worldwide cybercrime damage is expected to reach $6 trillion—double what it cost businesses in 2015. -
Making Microsoft Edge the most secure browser with Windows Defender Application Guard
Innovation in the attack space is constant as adversaries increase in both determination and sophistication. -

Best practices for securely moving workloads to Microsoft Azure
Azure is Microsoft’s cloud computing environment. -

Tapping the intelligent cloud to make security better and easier
There has been a distinct shift in my conversations with customers over the last year. -
Securing the modern workplace with Microsoft 365 threat protection – part 2
This post is authored by Debraj Ghosh, Senior Product Marketing Manager, Microsoft 365 Security. -

Securing the modern workplace with Microsoft 365 threat protection – part 3
This post is authored by Debraj Ghosh, Senior Product Marketing Manager, Microsoft 365 Security. -
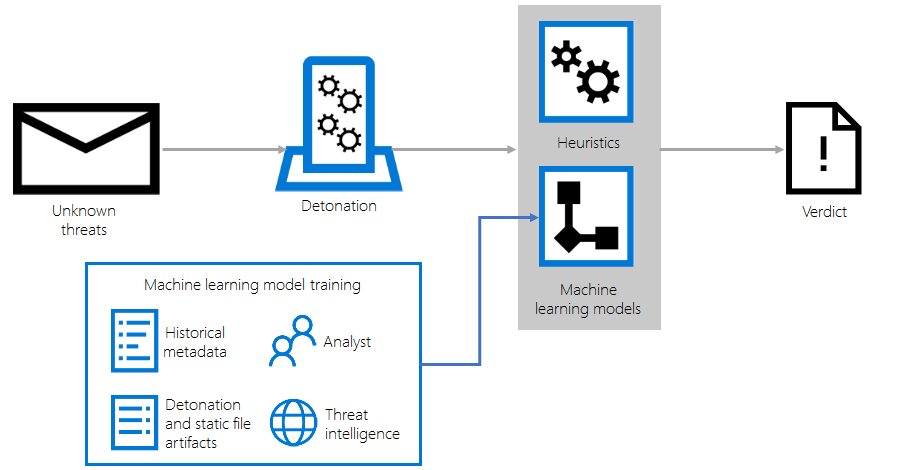
Enhancing Office 365 Advanced Threat Protection with detonation-based heuristics and machine learning
Office 365 Advanced Threat Protection (ATP) uses a comprehensive and multi-layered solution to protect mailboxes, files, online storage, and applications against a wide range of threats. -
Securing the modern workplace with Microsoft 365 threat protection – part 4
This post is authored by Debraj Ghosh, Senior Product Marketing Manager, Microsoft 365 Security. -
Data classification and protection now available for structured data in SQL
This post is authored by Gilad Mittelman, Senior Program Manager, SQL Data Security.





