

Threat actors
Microsoft actively discovers and tracks threat actors across observed state-sponsored, ransomware, and criminal activities. Get insights from the 60 nation-state actors, 50 ransomware groups, and hundreds of other attackers we’ve tracked.
Refine results
Topic
Products and services
Publish date
-
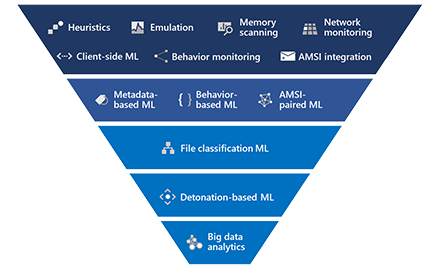
 Two new machine learning protection features within the behavioral blocking and containment capabilities in Microsoft Defender ATP specialize in detecting threats by analyzing behavior, adding new layers of protection after an attack has started running.
Two new machine learning protection features within the behavioral blocking and containment capabilities in Microsoft Defender ATP specialize in detecting threats by analyzing behavior, adding new layers of protection after an attack has started running. -

Insights from one year of tracking a polymorphic threat
We discovered the polymoprhic threat Dexphot in October 2018. -

Inside Microsoft 365 Defender: Attack modeling for finding and stopping lateral movement
Microsoft Threat Protection uses a data-driven approach for identifying lateral movement, combining industry-leading optics, expertise, and data science to deliver automated discovery of some of the most critical threats today. -

Blue teams helping red teams: A tale of a process crash, PowerShell, and the MITRE ATT&CK evaluation
Inspired by MITRE’s transparency in publishing the payloads and tools used in the attack simulation, we’ll describe the mystery that is Step 19 and tell a story about how blue teams, once in a while, can share important learnings for red teams. -

Inside Microsoft 365 Defender: Mapping attack chains from cloud to endpoint
In the first blog in the Inside Microsoft Threat Protection series, we will show how MTP provides unparalleled end-to-end visibility into the activities of nation-state level attacks like HOLMIUM. -

Industry-wide partnership on threat-informed defense improves security for all
MITRE Engenuity’s Center for Threat-Informed Defense has published a library of detailed plans for emulating the threat actor FIN6 (which Microsoft tracks as TAAL). -

Trickbot disrupted
Microsoft took action against the Trickbot botnet, disrupting one of the world’s most persistent malware operations. -

Threat actor leverages coin miner techniques to stay under the radar – here’s how to spot them
BISMUTH, which has been running increasingly complex cyberespionage attacks as early as 2012, deployed Monero coin miners in campaigns from July to August 2020. -

EDR in block mode stops IcedID cold
Endpoint detection and response (EDR) in block mode in Microsoft Defender for Endpoint turns EDR detections into real-time blocking of threats. -

ZINC attacks against security researchers
In recent months, Microsoft has detected cyberattacks targeting security researchers by an actor we track as ZINC. -

What tracking an attacker email infrastructure tells us about persistent cybercriminal operations
Sweeping research into massive attacker infrastructures, as well as our real-time monitoring of malware campaigns and attacker activity, directly inform Microsoft security solutions, allowing us to build or improve protections that block malware campaigns and other email threats, both current and future, as well as provide enterprises with the tools for investigating and responding to email campaigns in real-time. -

Microsoft open sources CodeQL queries used to hunt for Solorigate activity
We are sharing the CodeQL queries that we used to analyze our source code at scale and rule out the presence of the code-level indicators of compromise (IoCs) and coding patterns associated with Solorigate so that other organizations may perform a similar analysis.





