

Influence operations
Cyber influence operations aim to erode trust, increase polarization, and threaten democratic processes. Explore how nation states are using traditional cyberattack tools in coordinated influence campaigns.
Refine results
Topic
Products and services
Publish date
-
(Note: Read about Windows Defender Antivirus cloud protection service in this blog entry: Windows Defender Antivirus cloud protection service: Advanced real-time defense against never-before-seen malware.
-
A brief discourse on ‘Changing browsing experience’
Protecting the modern workplace from a wide range of undesirable software Our evaluation criteria describe the characteristics and behavior of malware and potentially unwanted applications and guide the proper identification of threats. -

Adding transparency and context into industry AV test results
Corporate Vice President Brad Anderson recently shared his insights on how Windows Defender Advanced Threat Protection (Windows Defender ATP) evolved to achieve important quality milestones. -
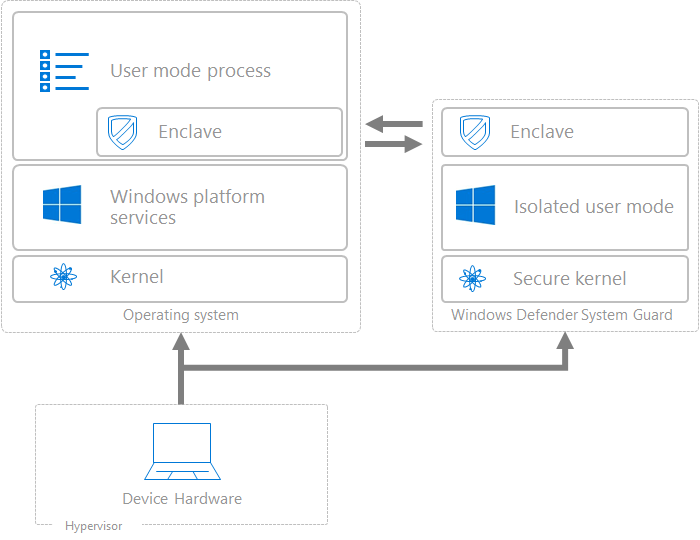
Virtualization-based security (VBS) memory enclaves: Data protection through isolation
The escalating sophistication of cyberattacks is marked by the increased use of kernel-level exploits that attempt to run malware with the highest privileges and evade security solutions and software sandboxes. -

March-April 2018 test results: More insights into industry AV tests
In a previous post, in the spirit of our commitment to delivering industry-leading protection, customer choice, and transparency on the quality of our solutions, we shared insights and context into the results of AV-TEST’s January-February 2018 test cycle. -
Partnering with the industry to minimize false positives
Every day, antivirus capabilities in Microsoft Defender Advanced Threat Protection (Microsoft Defender ATP) protect millions of customers from threats. -

Microsoft AI competition explores the next evolution of predictive technologies in security
Predictive technologies are already effective at detecting and blocking malware at first sight. -

DART: the Microsoft cybersecurity team we hope you never meet
Meet Microsoft’s Detection and Response Team (DART) and read their advice that may help you avoid working with them in future. -

From unstructured data to actionable intelligence: Using machine learning for threat intelligence
Machine learning and natural language processing can automate the processing of unstructured text for insightful, actionable threat intelligence. -

Deep learning rises: New methods for detecting malicious PowerShell
We adopted a deep learning technique that was initially developed for natural language processing and applied to expand Microsoft Defender ATP’s coverage of detecting malicious PowerShell scripts, which continue to be a critical attack vector. -

TLS version enforcement capabilities now available per certificate binding on Windows Server 2019
Microsoft is pleased to announce a powerful new feature in Windows to make your transition to a TLS 1. -

Collaborative innovation on display in Microsoft’s insider risk management strategy
Partnering with organizations like Carnegie Mellon University allows us to bring their rich research and insights to our products and services, so customers can fully benefit from our breadth of signals.





