

Influence operations
Cyber influence operations aim to erode trust, increase polarization, and threaten democratic processes. Explore how nation states are using traditional cyberattack tools in coordinated influence campaigns.
Refine results
Topic
Products and services
Publish date
-
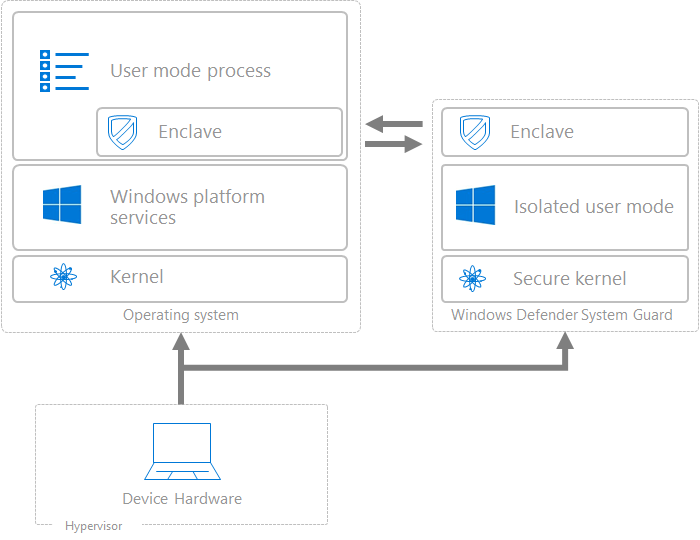
 The escalating sophistication of cyberattacks is marked by the increased use of kernel-level exploits that attempt to run malware with the highest privileges and evade security solutions and software sandboxes.
The escalating sophistication of cyberattacks is marked by the increased use of kernel-level exploits that attempt to run malware with the highest privileges and evade security solutions and software sandboxes. -

Adding transparency and context into industry AV test results
Corporate Vice President Brad Anderson recently shared his insights on how Windows Defender Advanced Threat Protection (Windows Defender ATP) evolved to achieve important quality milestones. -
A brief discourse on ‘Changing browsing experience’
Protecting the modern workplace from a wide range of undesirable software Our evaluation criteria describe the characteristics and behavior of malware and potentially unwanted applications and guide the proper identification of threats. -
Microsoft cloud protection
(Note: Read about Windows Defender Antivirus cloud protection service in this blog entry: Windows Defender Antivirus cloud protection service: Advanced real-time defense against never-before-seen malware. -

New Microsoft Threat Modeling Tool 2014 Now Available
Today we’re announcing the release of the <a href=”http://download.
-
Why does my AV software keep turning off?
Bob writes: My antivirus software keeps turning off and I can’t get it back on. -
Microsoft’s Free Security Tools – Microsoft Assessment and Planning (MAP) Toolkit
This article in our<a href=”https://blogs.
-
Microsoft Free Security Tools – Microsoft Baseline Security Analyzer
This article in our <a href=”/b/security/archive/2012/07/31/microsoft-s-free-security-tools-series-introduction.
-
Microsoft’s Free Security Tools – Summary
In July, we kicked off a blog series focused on “<a href=”/b/security/archive/2012/07/31/microsoft-s-free-security-tools-series-introduction.
-
Microsoft’s Free Security Tools – Portqry
This article in our <a href=”/b/security/archive/2012/07/31/microsoft-s-free-security-tools-series-introduction.
-
Microsoft’s Free Security Tools – Windows Defender Offline
This article in our <a href=”/b/security/archive/2012/07/31/microsoft-s-free-security-tools-series-introduction.
-
Fundamentals of Cloud Service Reliability
As the adoption of cloud computing continues to rise, and customers demand 24/7 access to their services and data, reliability remains a challenge for cloud service providers everywhere.





