

Cyberattacker techniques, tools, and infrastructure
Cyberattackers constantly evolve their techniques, tools, and infrastructure to launch increasingly complex attacks. Learn about the latest tactics and how to detect, disrupt, and defend against them.
Refine results
Topic
Products and services
Publish date
-
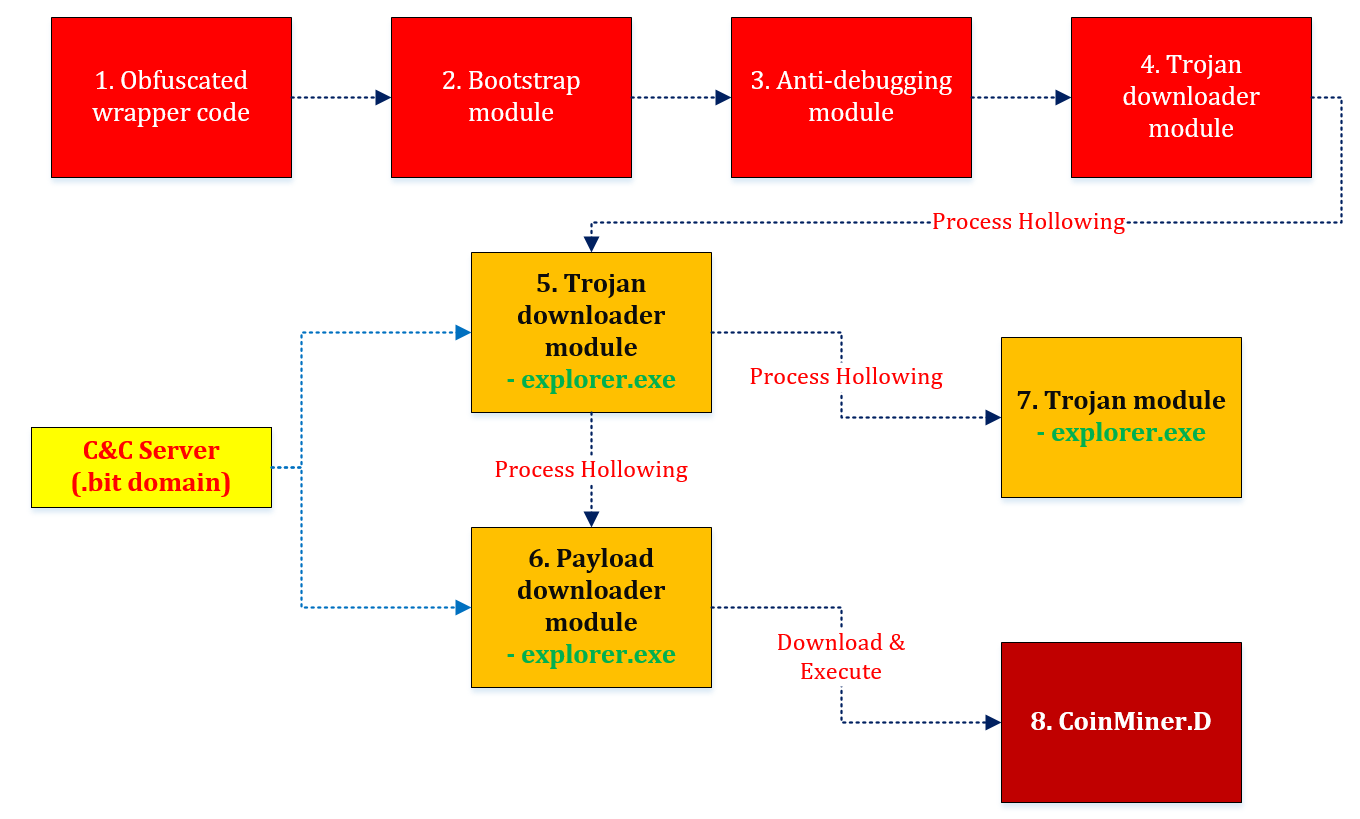
 Dofoil is a sophisticated threat that attempted to install coin miner malware on hundreds of thousands of computers in March, 2018.
Dofoil is a sophisticated threat that attempted to install coin miner malware on hundreds of thousands of computers in March, 2018. -
Teaming up in the war on tech support scams
Beyond customer education, the scale and complexity of tech support scams require cooperation and broad partnerships across the industry. -
Hawkeye Keylogger – Reborn v8: An in-depth campaign analysis
Hawkeye Keylogger is an info-stealing malware that’s being sold as malware-as-a-service. -
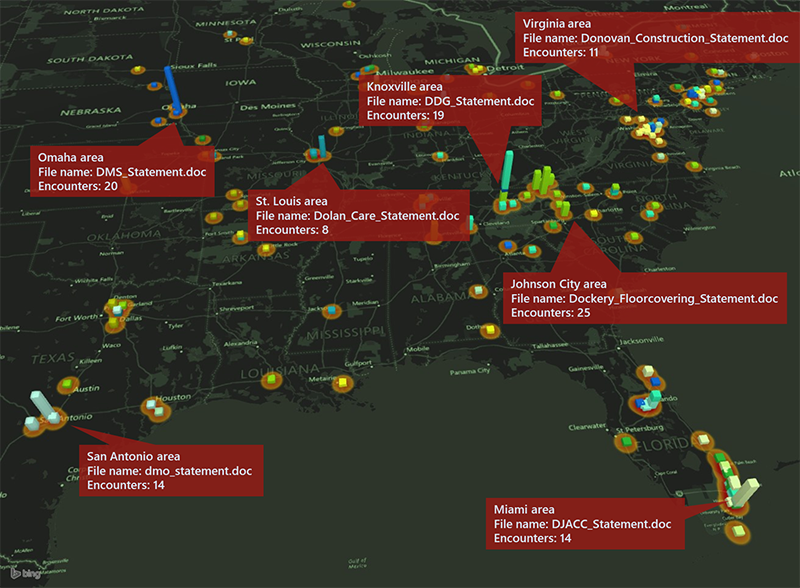
Small businesses targeted by highly localized Ursnif campaign
In social engineering attacks, is less really more? A new malware campaign puts that to the test by targeting home users and small businesses in specific US cities. -

Windows Defender Antivirus can now run in a sandbox
Windows Defender Antivirus has hit a new milestone: the built-in antivirus capabilities on Windows can now run within a sandbox. -
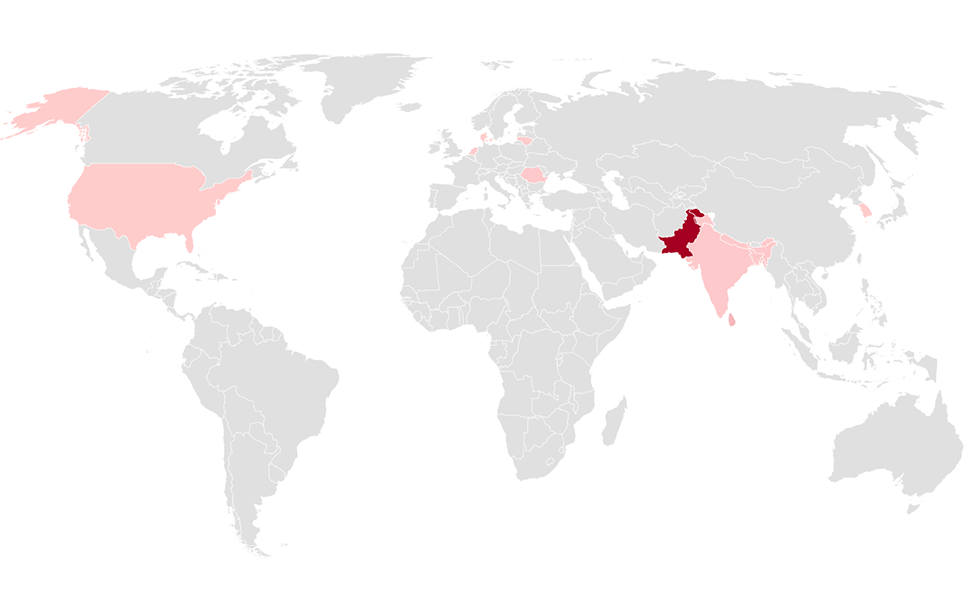
Attack uses malicious InPage document and outdated VLC media player to give attackers backdoor access to targets
Our analysis of a targeted attack that used a language-specific word processor shows why it’s important to understand and protect against small-scale and localized attacks as well as broad-scale malware campaigns. -
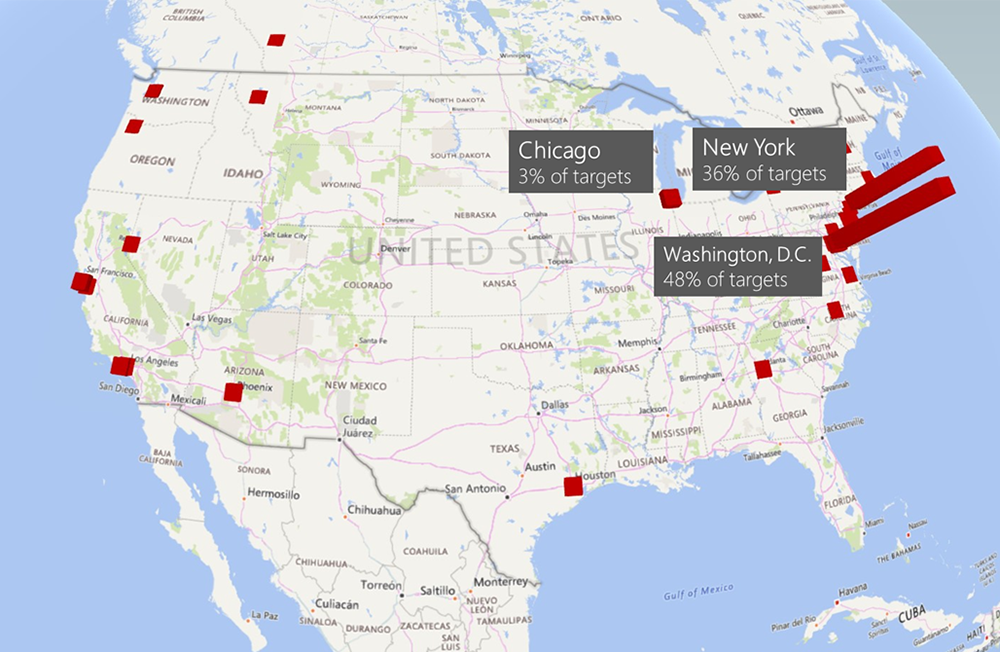
Analysis of cyberattack on U.S. think tanks, non-profits, public sector by unidentified attackers
Reuters recently reported a hacking campaign focused on a wide range of targets across the globe. -

Insights from the MITRE ATT&CK-based evaluation of Windows Defender ATP
In MITRE’s evaluation of endpoint detection and response solutions, Windows Defender Advanced Threat Protection demonstrated industry-leading optics and detection capabilities. -

Recommendations for deploying the latest Attack surface reduction rules for maximum impact
Attack surface reduction is a technique to remove or constrain exploitable behaviors in your systems. -

From alert to driver vulnerability: Microsoft Defender ATP investigation unearths privilege escalation flaw
Our discovery of two privilege escalation vulnerabilities in a driver highlights the strength of Microsoft Defender ATP’s sensors. -

Detecting credential theft through memory access modelling with Microsoft Defender ATP
Microsoft Defender ATP instruments memory-related function calls such as VirtualAlloc and VirtualProtect to catch in-memory attack techniques like reflective DLL loading. -

Dismantling a fileless campaign: Microsoft Defender ATP’s Antivirus exposes Astaroth attack
Advanced technologies in Microsoft Defender ATP’s Antivirus exposed and defeated a widespread fileless campaign that completely “lived off the land” throughout a complex attack chain that run the info-stealing backdoor Astaroth directly in memory





