Towards Safer Augmented Reality: Identifying, Evaluating, and Mitigating Security & Privacy Threats
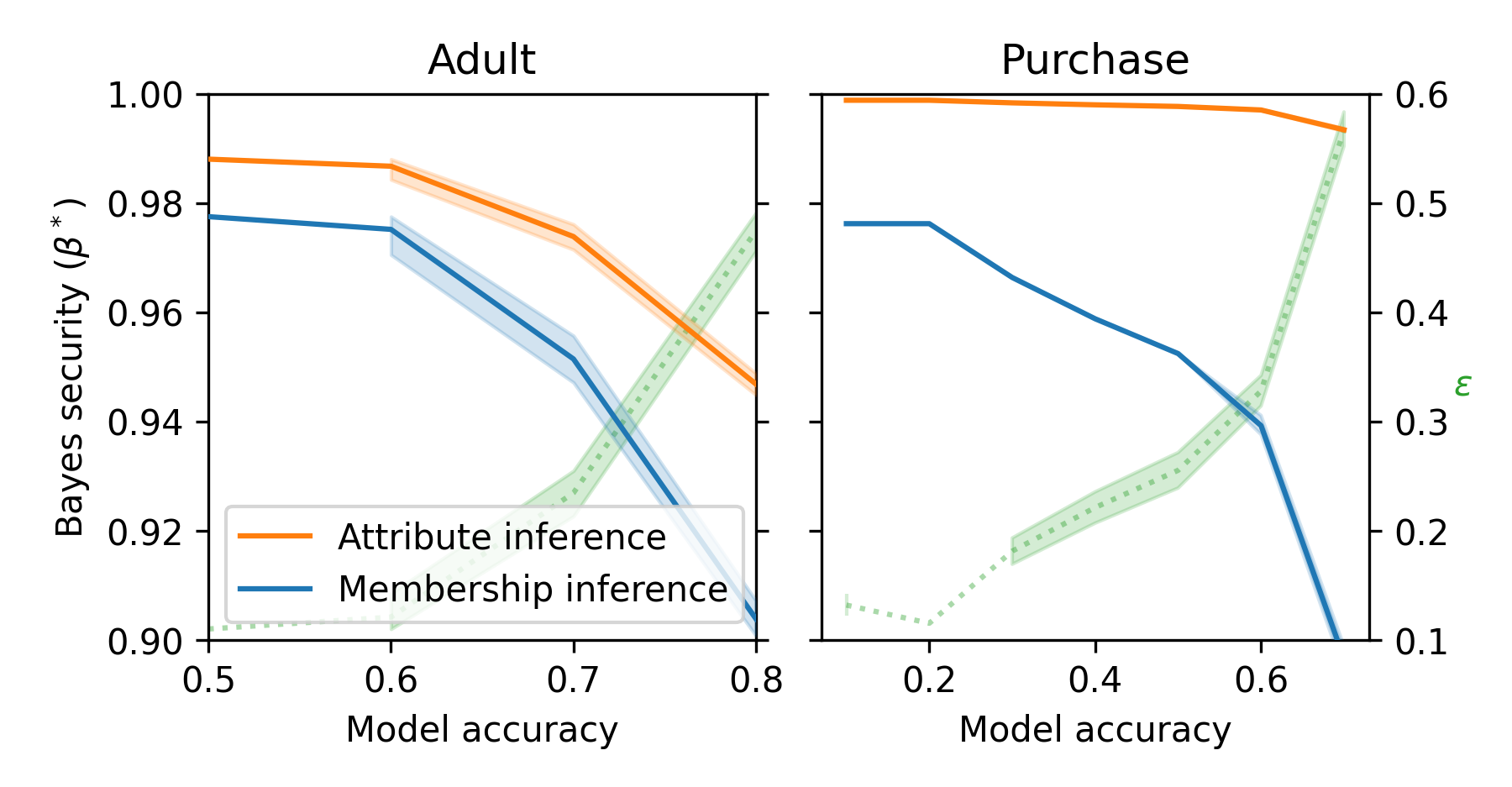
Augmented-reality (AR) technologies merge virtual content with users’ perceptions of the real-world environment. These technologies revolutionize how humans interact with the surrounding world, and enhance machine understanding of human behavior and physical spaces. As AR…
Hamming Quasi-Cyclic
In this talk, I will present the HQC scheme, which was recently selected by NIST as the second KEM protocol to be standardized within the Post-Quantum Cryptography standardization effort. HQC is a code-based scheme, using…
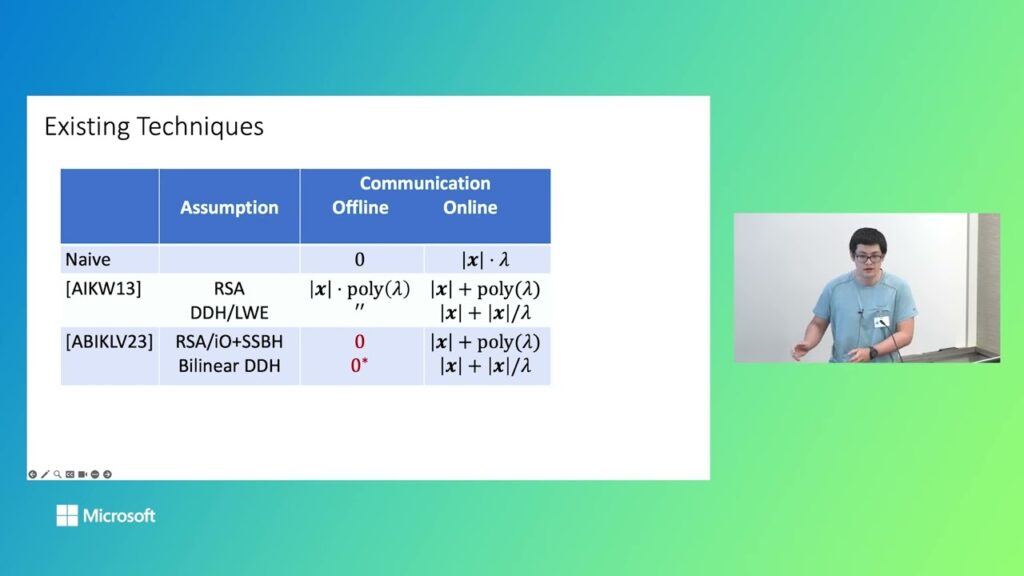
How to Compress Garbled Circuit Input Labels, Efficiently
Garbled circuit is a foundational primitive in both theory and practice of cryptography. Given (\hat{C}, K[x]), where \hat{C} is the garbling of a circuit C and K[x] = {K[i, x_i]} are the input labels for…
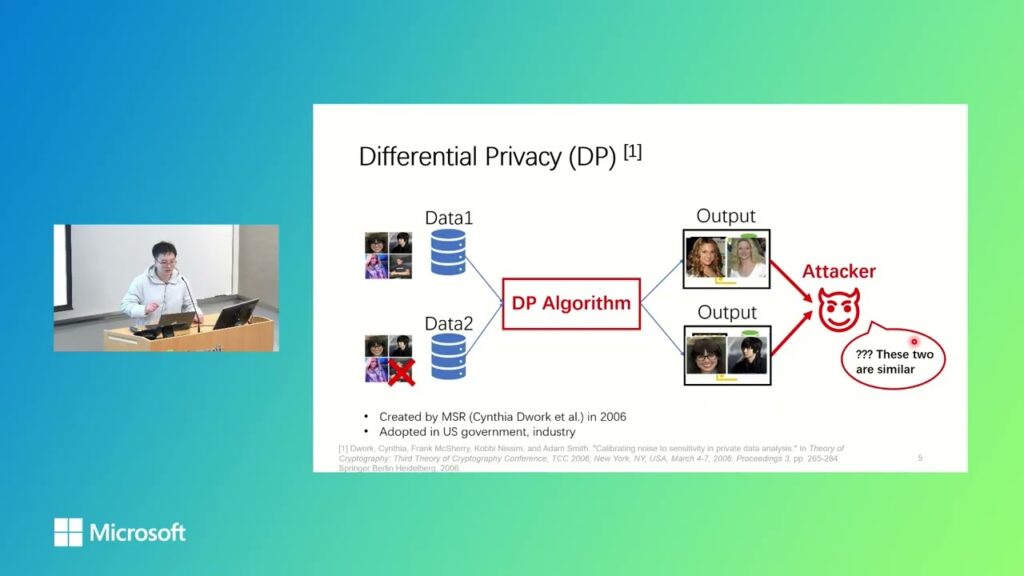
Differentially Private Synthetic Data without Training
Generating differentially private (DP) synthetic data that closely resembles original data while preserving user privacy is a scalable solution to address privacy concerns in today’s data-driven world. In this talk, I will introduce Private Evolution…
National AI Research Resource (NAIRR) Pilot
Microsoft is delighted to contribute as a lead supporter of the National AI Research Resource (NAIRR) pilot. (opens in new tab) The mission of the NAIRR pilot aligns with our commitment to broaden AI research…
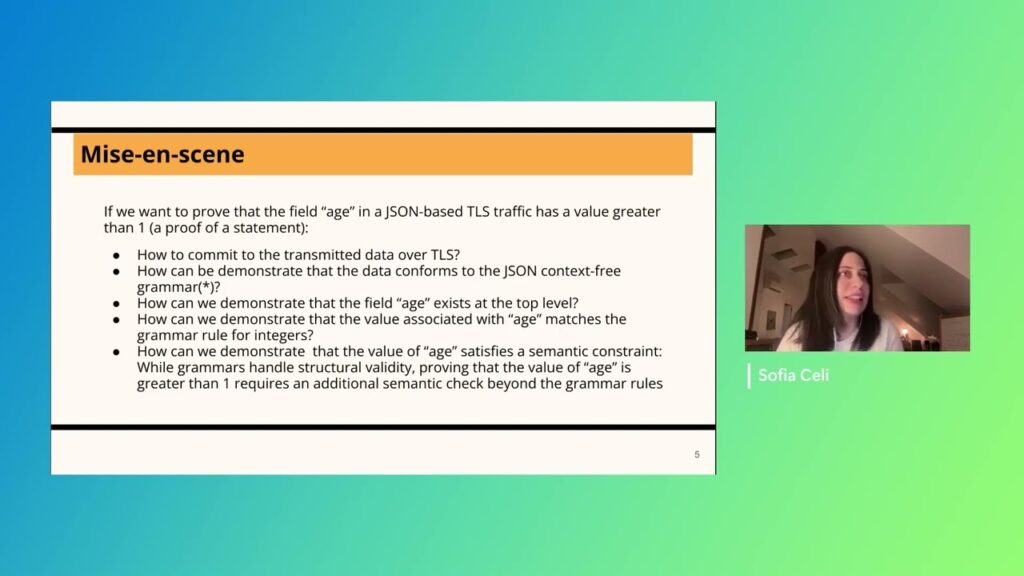
Attestations over TLS 1.3 and ZKP
The Transport Layer Security (TLS) protocol is fundamental for securing data transmission over the Internet, providing encrypted and authenticated channels that protect users’ data. However, certain scenarios require not only secure transmission but also the…